In today's interconnected world, remote access to IoT devices has become essential for businesses and individuals alike. However, using RemoteIoT behind a firewall on a Mac can pose challenges. It requires careful configuration to ensure secure and seamless connectivity without compromising network security. This article will guide you through the process step-by-step, ensuring your setup remains robust and protected.
RemoteIoT technology allows users to manage and monitor IoT devices from anywhere in the world. Whether you're a system administrator, developer, or tech enthusiast, understanding how to configure RemoteIoT behind a firewall on a Mac is crucial. This guide will provide practical solutions and expert advice to help you achieve this goal effectively.
As we delve deeper into the topic, we'll explore the technical aspects of setting up RemoteIoT, discuss potential security concerns, and offer actionable tips to ensure your setup is both functional and secure. By the end of this article, you'll have the knowledge and tools necessary to configure RemoteIoT on your Mac confidently.
Read also:Luke Combs Political Views A Comprehensive Exploration
Table of Contents
- Introduction to RemoteIoT and Firewalls
- Understanding Security Risks
- Setting Up RemoteIoT on Mac
- Configuring Firewalls for RemoteIoT
- Using VPNs for Enhanced Security
- Port Forwarding Techniques
- Common Issues and Troubleshooting
- Best Practices for Secure Connections
- Recommended Tools and Software
- Future Trends in RemoteIoT Technology
Introduction to RemoteIoT and Firewalls
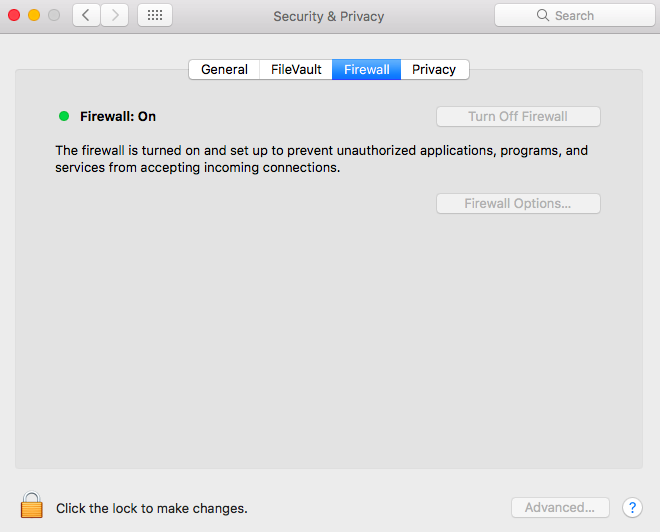
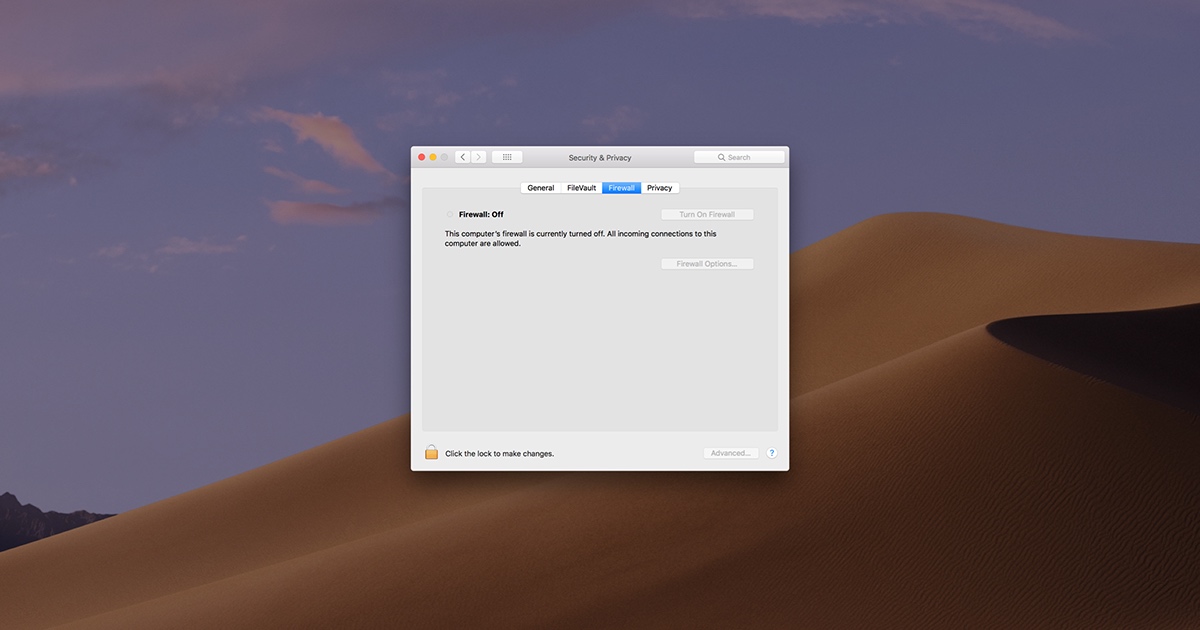
RemoteIoT technology enables users to access IoT devices remotely, which is particularly useful in scenarios where physical proximity is not possible. However, firewalls are designed to protect networks from unauthorized access, making it challenging to establish secure remote connections. Understanding the relationship between RemoteIoT and firewalls is critical for successful implementation.
Why Firewalls Are Important
Firewalls act as a barrier between your internal network and external threats. They filter incoming and outgoing traffic based on predefined security rules. When configuring RemoteIoT on a Mac, it's essential to ensure that your firewall settings allow necessary traffic while blocking potential threats.
- Firewalls protect against unauthorized access.
- They monitor and log traffic for analysis.
- Firewalls enhance overall network security.
Understanding Security Risks
Before diving into the technical aspects of setting up RemoteIoT, it's crucial to understand the potential security risks involved. These risks include unauthorized access, data breaches, and malware attacks. By addressing these concerns upfront, you can implement measures to mitigate them effectively.
Common Security Threats
Here are some of the most common security threats associated with RemoteIoT:
- Data interception during transmission.
- Unauthorized access to IoT devices.
- Vulnerabilities in outdated software.
Setting Up RemoteIoT on Mac
Configuring RemoteIoT on a Mac involves several steps. From installing the necessary software to configuring system preferences, each step is critical to ensuring a smooth setup process.
Step-by-Step Guide
Follow these steps to set up RemoteIoT on your Mac:
Read also:What Is Sam Elliotts Political Affiliation Uncovering The Truth About His Political Stance
- Install the RemoteIoT client software.
- Configure system preferences to allow remote connections.
- Test the connection to ensure everything is working correctly.
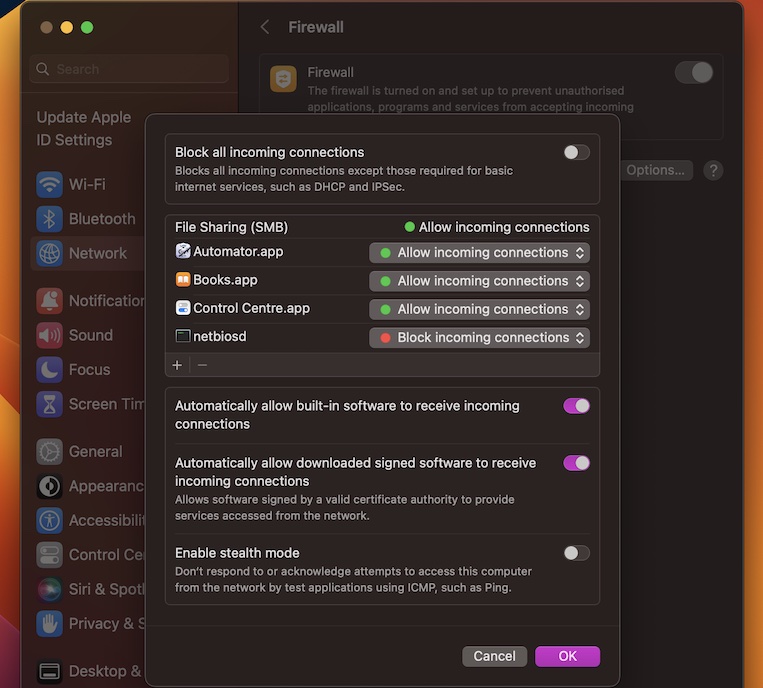
Configuring Firewalls for RemoteIoT
Firewall configuration is a critical aspect of setting up RemoteIoT behind a firewall. It involves adjusting firewall rules to allow specific traffic while maintaining overall network security.
Key Considerations
- Identify the ports used by RemoteIoT and ensure they are open.
- Set up inbound and outbound rules to allow necessary traffic.
- Regularly review and update firewall rules to adapt to changing security needs.
Using VPNs for Enhanced Security
Virtual Private Networks (VPNs) offer an additional layer of security when using RemoteIoT behind a firewall. They encrypt data transmissions, making it harder for attackers to intercept sensitive information.
Benefits of Using a VPN
- Encrypts data transmissions for enhanced security.
- Masks your IP address to protect your identity.
- Provides secure access to remote networks.
Port Forwarding Techniques
Port forwarding is a technique used to direct incoming traffic to specific devices within a network. When configuring RemoteIoT behind a firewall, port forwarding can help ensure that traffic reaches the intended IoT devices.
How to Set Up Port Forwarding
Follow these steps to set up port forwarding:
- Access your router's settings through a web browser.
- Locate the port forwarding section and configure the necessary settings.
- Test the connection to ensure port forwarding is working correctly.
Common Issues and Troubleshooting
Despite careful planning, issues can arise when setting up RemoteIoT behind a firewall. Understanding common problems and how to troubleshoot them can save time and frustration.
Troubleshooting Tips
- Check firewall logs for blocked traffic.
- Verify that all necessary ports are open.
- Ensure that the RemoteIoT client software is up to date.
Best Practices for Secure Connections
Adopting best practices is essential for maintaining secure RemoteIoT connections. These practices include regular software updates, strong password policies, and monitoring network activity.
Implementing Best Practices
- Regularly update software to patch security vulnerabilities.
- Enforce strong password policies to prevent unauthorized access.
- Monitor network activity for suspicious behavior.
Recommended Tools and Software
Several tools and software can assist in configuring and managing RemoteIoT connections. These tools can simplify the setup process and enhance overall security.
Top Tools for RemoteIoT
- Firewall management software for easy rule configuration.
- Network monitoring tools to detect and respond to threats.
- Encryption software to secure data transmissions.
Future Trends in RemoteIoT Technology
The field of RemoteIoT technology is rapidly evolving, with new innovations emerging regularly. Understanding future trends can help you stay ahead of the curve and prepare for upcoming changes in the industry.
Emerging Trends
- Increased adoption of AI-driven IoT solutions.
- Advancements in secure communication protocols.
- Growing emphasis on privacy and data protection.
Conclusion
In conclusion, configuring RemoteIoT behind a firewall on a Mac requires careful planning and execution. By following the steps outlined in this guide, you can ensure a secure and functional setup. Remember to adopt best practices, use recommended tools, and stay informed about future trends to maintain optimal performance and security.
We invite you to share your thoughts and experiences in the comments section below. If you found this article helpful, please consider sharing it with others. For more informative content, explore our other articles on technology and cybersecurity.