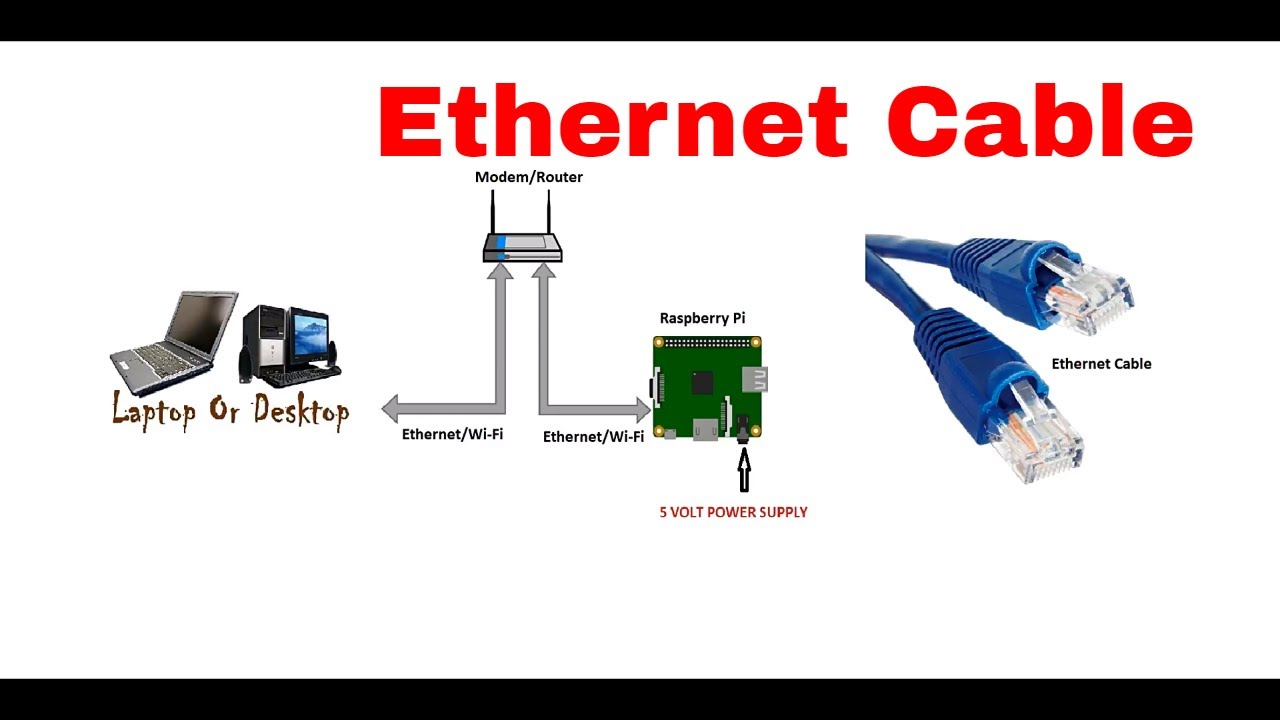
In today's interconnected world, securely connecting remote IoT devices using peer-to-peer (P2P) networks has become a critical need for tech enthusiasts and professionals alike. Whether you're managing a home automation system or developing a complex IoT infrastructure, ensuring secure communication is paramount. This guide focuses on setting up a secure P2P connection using a Raspberry Pi and downloading necessary components on a Mac.
Connecting IoT devices remotely can be challenging, especially when security is a top priority. The rise of smart homes, wearable tech, and industrial IoT solutions demands robust security measures. With the right tools and techniques, you can ensure that your data remains safe while maintaining seamless communication between devices.
This comprehensive guide explores the step-by-step process of setting up a secure P2P connection using a Raspberry Pi. We'll cover essential topics such as configuring the Raspberry Pi, securing the connection, and downloading necessary files on a Mac. By the end of this article, you'll have a clear understanding of how to implement a secure IoT P2P network.
Read also:Why Did Joe Leave Impractical Jokers The Untold Story
Table of Contents
- Introduction to Secure IoT Connections
- Setting Up Your Raspberry Pi
- Securing the Connection
- Understanding P2P Networking
- Downloading Necessary Files on Mac
- Essential Tools and Software
- Troubleshooting Common Issues
- Best Practices for IoT Security
- Future Trends in IoT Security
- Conclusion and Call to Action
Introduction to Secure IoT Connections
Why Security Matters in IoT
IoT devices are vulnerable to various security threats, including unauthorized access, data breaches, and malware attacks. A secure connection is essential to protect sensitive information and ensure the integrity of your network. By implementing robust security measures, you can safeguard your devices and maintain trust with users.
Key aspects of secure IoT connections include encryption, authentication, and regular software updates. Understanding these elements is crucial for anyone working with IoT devices.
Setting Up Your Raspberry Pi
Hardware Requirements
Before diving into the setup process, ensure you have the following hardware components:
- Raspberry Pi (Model 3B+ or later)
- MicroSD card with at least 16GB capacity
- Power supply with appropriate voltage and current
- USB keyboard and mouse
- HDMI monitor or TV
Having the right hardware is the foundation of a successful setup. Ensure all components are compatible with your Raspberry Pi model.
Securing the Connection
Encryption Protocols
Implementing encryption protocols is vital for securing IoT P2P connections. Some of the most commonly used protocols include:
Read also:David Muir The Inspiring Journey Of An Awardwinning Journalist
- TLS (Transport Layer Security)
- SSL (Secure Sockets Layer)
- SSH (Secure Shell)
Each protocol has its strengths and weaknesses, so choose the one that best fits your needs. For example, SSH is ideal for remote command-line access, while TLS is better suited for securing data transmission.
Understanding P2P Networking
What is P2P Networking?
P2P networking allows devices to communicate directly with each other without relying on a central server. This decentralized approach offers several advantages, including improved performance, reduced latency, and enhanced security. By eliminating the need for a central server, P2P networks minimize the risk of single points of failure.
Key benefits of P2P networking include:
- Increased scalability
- Lower infrastructure costs
- Improved data privacy
Downloading Necessary Files on Mac
Steps to Download Files on Mac
Downloading files on a Mac is a straightforward process. Follow these steps to ensure a smooth experience:
- Open Safari or your preferred browser
- Navigate to the official Raspberry Pi website
- Download the latest version of Raspberry Pi OS
- Use a tool like Etcher to write the OS image to your MicroSD card
By following these steps, you can ensure that your Raspberry Pi is equipped with the latest software and security updates.
Essential Tools and Software
Software for Managing IoT Devices
Several tools and software can help you manage your IoT devices more effectively:
- Home Assistant: A popular open-source platform for home automation
- Node-RED: A visual tool for wiring together hardware devices, APIs, and online services
- Mosquitto: An open-source MQTT broker for managing communication between devices
These tools provide powerful features for monitoring, controlling, and securing your IoT devices.
Troubleshooting Common Issues
Common Problems and Solutions
When setting up a secure IoT P2P connection, you may encounter various issues. Here are some common problems and their solutions:
- Connection Issues: Ensure all devices are on the same network and check firewall settings.
- Software Errors: Update all software components to the latest versions.
- Hardware Failures: Verify that all hardware components are functioning correctly.
By addressing these issues promptly, you can maintain a stable and secure IoT network.
Best Practices for IoT Security
Implementing Security Measures
To enhance the security of your IoT devices, consider the following best practices:
- Use strong, unique passwords for all devices
- Enable two-factor authentication whenever possible
- Regularly update firmware and software
- Monitor network activity for suspicious behavior
Adopting these practices will significantly reduce the risk of security breaches and protect your devices from unauthorized access.
Future Trends in IoT Security
Emerging Technologies
The future of IoT security is shaped by emerging technologies such as blockchain, artificial intelligence, and quantum computing. These innovations offer promising solutions for addressing current security challenges:
- Blockchain: Provides decentralized, tamper-proof ledgers for secure data storage
- AI: Enables advanced threat detection and automated response systems
- Quantum Computing: Offers unparalleled computational power for encryption and decryption
Staying informed about these trends will help you prepare for the future of IoT security.
Conclusion and Call to Action
Securing remote IoT P2P connections using a Raspberry Pi and downloading necessary files on a Mac is a multifaceted process that requires attention to detail and adherence to best practices. By following the steps outlined in this guide, you can ensure that your IoT network remains secure and functional.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, explore other articles on our site for more insights into IoT security and related topics. Together, we can build a safer and more connected world.
References: