In today's digital age, remote IoT (Internet of Things) devices require secure and efficient methods to connect and manage data over the internet. One of the most reliable ways to achieve this is through RemoteIoT SSH AWS Example, leveraging the power of Secure Shell (SSH) and Amazon Web Services (AWS). This combination ensures robust security, scalability, and ease of deployment for IoT applications.
As IoT continues to expand, managing remote devices has become a critical challenge for businesses and developers. The need for secure communication channels is paramount, especially when transmitting sensitive data. RemoteIoT SSH AWS Example provides a practical solution to this issue, offering a secure and scalable way to interact with IoT devices hosted on AWS infrastructure.
This article will explore the intricacies of RemoteIoT SSH AWS Example, including its setup, benefits, and best practices. Whether you're a developer, IT professional, or someone interested in IoT technology, this guide will equip you with the knowledge to implement secure remote connections for your IoT projects.
Read also:What Is Sam Elliotts Political Affiliation Uncovering The Truth About His Political Stance
Table of Contents
- Introduction to RemoteIoT SSH AWS Example
- What is SSH?
- Benefits of Using AWS for RemoteIoT
- Step-by-Step Setup Process
- Security Considerations for RemoteIoT SSH AWS
- Scaling IoT Devices with AWS
- Common Issues and Troubleshooting
- Real-World Examples of RemoteIoT SSH AWS
- Best Practices for RemoteIoT SSH AWS Example
- Future Trends in IoT and AWS Integration
Introduction to RemoteIoT SSH AWS Example
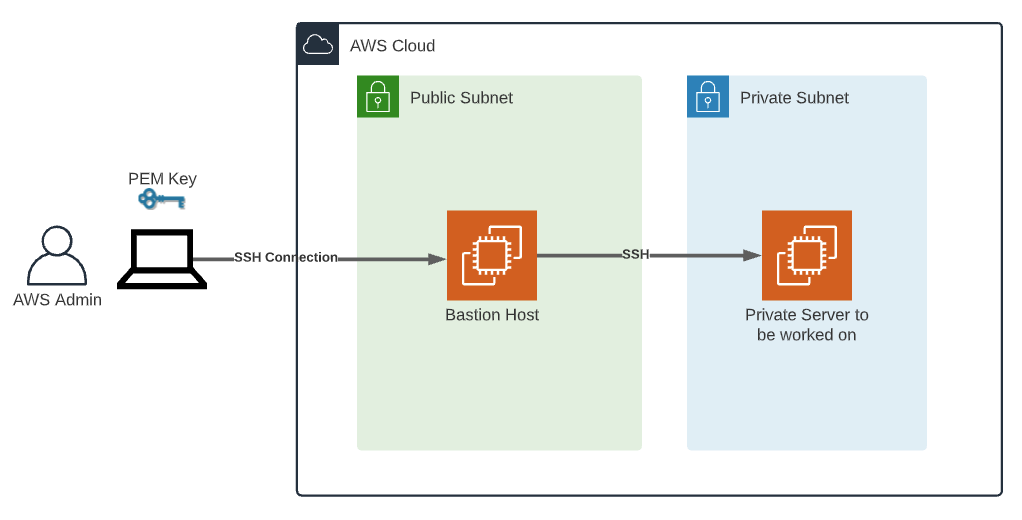
The concept of RemoteIoT SSH AWS Example revolves around establishing secure connections between IoT devices and cloud servers using SSH protocols on AWS infrastructure. This setup ensures that data transmission remains encrypted and protected from unauthorized access.
Why is RemoteIoT SSH AWS Example important? In today's interconnected world, IoT devices often operate in remote locations, making physical access impossible. SSH provides a secure method for remote management, while AWS offers the scalability and reliability needed for enterprise-level applications.
This section will delve into the foundational aspects of RemoteIoT SSH AWS Example, including its architecture, components, and the role of SSH and AWS in modern IoT ecosystems.
What is SSH?
Understanding Secure Shell (SSH)
Secure Shell (SSH) is a cryptographic network protocol designed to provide secure communication over unsecured networks. It is widely used for remote command-line logins and data transfer between systems. SSH ensures data integrity, confidentiality, and authentication, making it an ideal choice for managing IoT devices remotely.
Key Features of SSH:
- Encryption: SSH encrypts all data transmitted between the client and server, preventing eavesdropping.
- Authentication: It supports various authentication methods, including password-based and public key authentication.
- Port Forwarding: SSH allows secure tunneling of other protocols, such as HTTP or FTP.
Benefits of Using AWS for RemoteIoT
Amazon Web Services (AWS) is a leader in cloud computing, offering a wide range of services tailored for IoT applications. By integrating RemoteIoT SSH AWS Example, businesses can enjoy several advantages:
Read also:Gail Ogrady A Comprehensive Guide To Her Career Achievements And Legacy
- Scalability: AWS allows seamless scaling of IoT devices based on demand, ensuring optimal performance.
- Global Infrastructure: With data centers worldwide, AWS ensures low latency and high availability for IoT applications.
- Security: AWS provides robust security features, including IAM roles, VPCs, and encryption, to protect IoT data.
Step-by-Step Setup Process
Configuring RemoteIoT SSH AWS Example
Setting up RemoteIoT SSH AWS Example involves several steps, including configuring AWS services, generating SSH keys, and establishing secure connections. Below is a detailed guide:
- Create an AWS Account: Sign up for an AWS account if you don't already have one.
- Set Up EC2 Instance: Launch an EC2 instance to host your IoT application. Choose an appropriate AMI and instance type.
- Generate SSH Keys: Use the AWS Management Console or SSH tools to generate key pairs for secure authentication.
- Configure Security Groups: Define security groups to allow SSH access while restricting unauthorized traffic.
- Connect to EC2 Instance: Use an SSH client to connect to your EC2 instance and begin managing IoT devices.
Security Considerations for RemoteIoT SSH AWS
Security is a top priority when implementing RemoteIoT SSH AWS Example. Below are some essential considerations:
- Use Strong Passwords: Ensure all accounts have strong, unique passwords to prevent brute-force attacks.
- Enable Two-Factor Authentication (2FA): Add an extra layer of security by requiring 2FA for SSH access.
- Regularly Update Systems: Keep your EC2 instances and IoT devices updated with the latest security patches.
Scaling IoT Devices with AWS
Managing Large-Scale IoT Deployments
AWS offers several tools and services to manage large-scale IoT deployments, including AWS IoT Core and AWS Lambda. These services enable efficient device management, data processing, and automation. By leveraging these tools, businesses can scale their IoT applications without compromising performance or security.
Common Issues and Troubleshooting
While RemoteIoT SSH AWS Example is a powerful solution, users may encounter common issues such as connection errors or authentication failures. Below are some troubleshooting tips:
- Check SSH Key Permissions: Ensure the correct permissions are set for your SSH keys.
- Verify Security Groups: Confirm that security groups allow SSH traffic on the appropriate port.
- Test Connectivity: Use tools like ping or traceroute to diagnose network issues.
Real-World Examples of RemoteIoT SSH AWS
Several industries have successfully implemented RemoteIoT SSH AWS Example for various applications. For instance, smart agriculture companies use this setup to monitor and control remote sensors, while manufacturing firms leverage it for predictive maintenance. These examples demonstrate the versatility and effectiveness of RemoteIoT SSH AWS Example in real-world scenarios.
Best Practices for RemoteIoT SSH AWS Example
Maximizing Security and Efficiency
To get the most out of RemoteIoT SSH AWS Example, consider the following best practices:
- Implement Role-Based Access Control (RBAC): Restrict access to IoT devices based on user roles and responsibilities.
- Monitor Logs Regularly: Analyze SSH logs to detect and respond to potential security threats.
- Use Automated Scripts: Automate routine tasks, such as device updates and backups, to save time and reduce errors.
Future Trends in IoT and AWS Integration
As IoT technology continues to evolve, the integration of RemoteIoT SSH AWS Example is expected to play a pivotal role in shaping future trends. Emerging technologies such as edge computing and 5G networks will enhance the capabilities of IoT applications, enabling faster and more reliable connections.
In conclusion, RemoteIoT SSH AWS Example offers a secure and scalable solution for managing IoT devices remotely. By following the guidelines outlined in this article, businesses and developers can harness the full potential of this powerful combination to drive innovation and growth in the IoT landscape.
Conclusion
This comprehensive guide has explored the concept of RemoteIoT SSH AWS Example, its benefits, setup process, and best practices. Implementing this solution can significantly enhance the security and efficiency of your IoT applications. We encourage readers to share their thoughts and experiences in the comments section below and explore other related articles on our website for further insights.