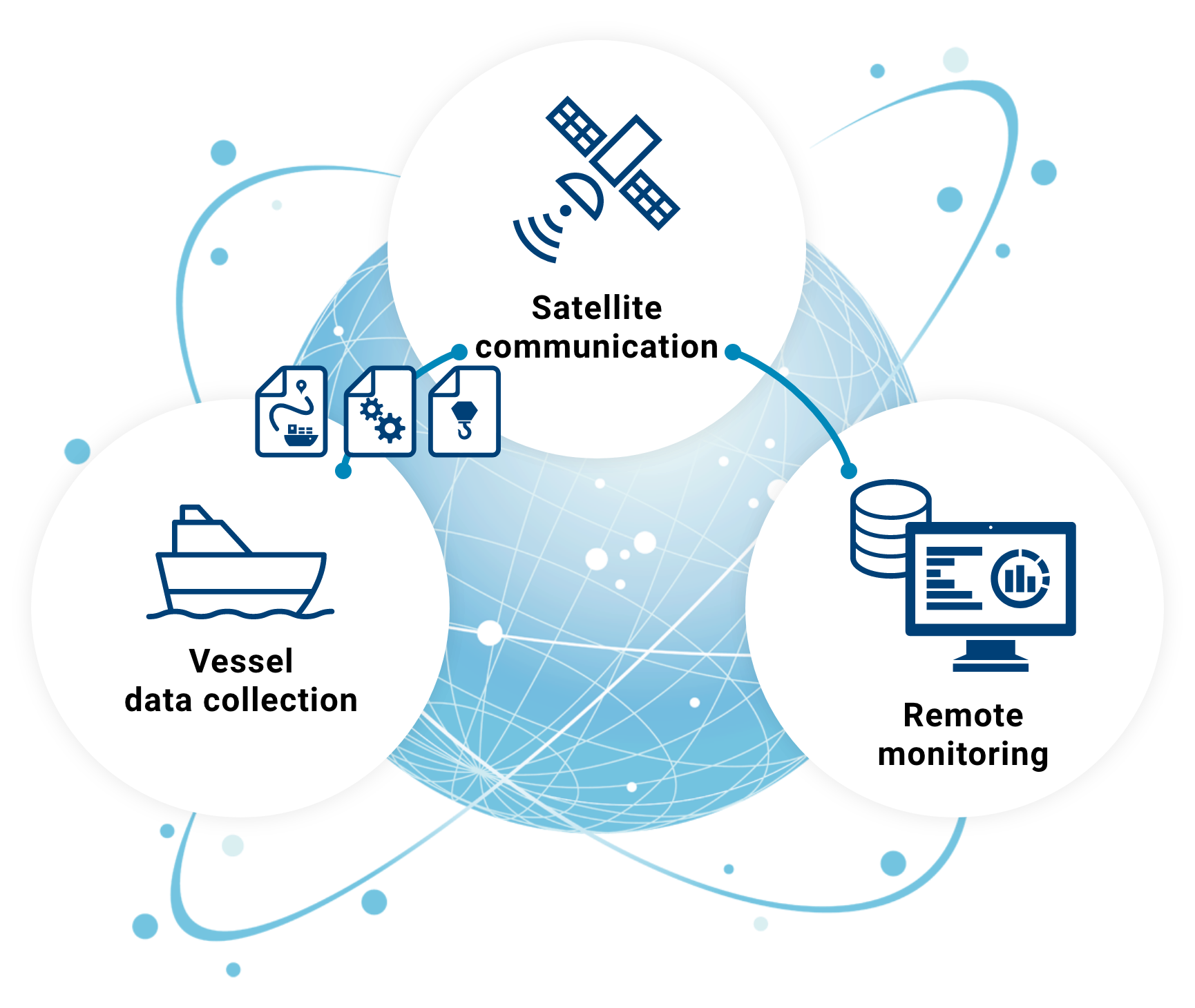
In today's digital age, the ability to remotely control devices behind firewalls is becoming increasingly important for businesses and individuals alike. Whether you're managing a remote workforce or accessing a secure network from afar, understanding how remote control devices function behind firewalls can significantly enhance productivity and security. This article delves into the intricacies of this technology, providing actionable insights and expert advice.
As technology evolves, remote access has become an essential component of modern operations. However, ensuring secure connectivity while maintaining robust firewall protections remains a challenge. This guide aims to demystify the process of controlling devices remotely without compromising security.
From understanding the basics of firewalls to exploring advanced techniques for secure remote access, this article covers everything you need to know about remote control devices behind firewalls. By the end, you'll have a comprehensive understanding of the tools, strategies, and best practices involved in this critical area of IT management.
Read also:The Suite Life Of Zack And Cody Justin Baldoni A Deep Dive Into The Iconic Disney Channel Series
Table of Contents
- Introduction to Firewalls
- Basics of Remote Control Devices
- Challenges of Remote Control Behind Firewalls
- Solutions for Remote Access
- Security Considerations
- Tools for Remote Control
- Implementing Remote Control Safely
- Best Practices for Remote Access
- Future Trends in Remote Control Technology
- Conclusion
Introduction to Firewalls
A firewall is a critical component of network security, acting as a barrier between trusted and untrusted networks. It monitors and controls incoming and outgoing network traffic based on predetermined security rules. Firewalls are essential for protecting sensitive data and preventing unauthorized access to internal networks.
Understanding how firewalls work is crucial when discussing remote control devices behind firewalls. Firewalls can block or allow traffic based on IP addresses, ports, protocols, and other criteria. This functionality ensures that only authorized users and devices can access the network.
However, firewalls can also pose challenges for remote access, as they may restrict or block necessary connections. Balancing security with accessibility is key to effectively managing remote control devices in a secure environment.
Basics of Remote Control Devices
Remote control devices allow users to operate and manage systems from a distance. These devices can range from simple tools for controlling home appliances to sophisticated software for managing enterprise networks. The ability to control devices remotely is particularly valuable in scenarios where physical access is impractical or impossible.
Key features of remote control devices include:
- Real-time monitoring and management
- Support for multiple operating systems and platforms
- Encryption and secure communication protocols
- User authentication and access control
When combined with firewalls, remote control devices offer a powerful solution for secure and efficient network management. However, proper configuration and implementation are essential to ensure both functionality and security.
Read also:Redmond Oneal 2025 Exploring The Future Of Innovation
Challenges of Remote Control Behind Firewalls
Controlling devices behind firewalls presents several challenges. Firewalls are designed to restrict unauthorized access, which can inadvertently block legitimate remote connections. Common challenges include:
- Port Restrictions: Firewalls often block specific ports required for remote access.
- IP Whitelisting: Limiting access to specific IP addresses can complicate remote operations.
- Authentication Issues: Ensuring secure authentication without compromising ease of use.
- Performance Degradation: Firewalls can introduce latency or reduce connection speeds.
Addressing these challenges requires a combination of technical expertise and strategic planning. Solutions such as port forwarding, IP whitelisting, and secure authentication protocols can help overcome these obstacles while maintaining robust security.
Solutions for Remote Access
Using a Virtual Private Network (VPN)
A Virtual Private Network (VPN) is one of the most effective solutions for remote control devices behind firewalls. A VPN creates a secure, encrypted tunnel between the remote device and the internal network, allowing users to access resources as if they were physically connected.
Key benefits of using a VPN include:
- Enhanced security through encryption
- Improved access control and user authentication
- Reduced risk of data interception and unauthorized access
When implementing a VPN, it's important to choose a reliable provider and configure the network properly to ensure optimal performance and security.
SSH Tunneling
SSH (Secure Shell) tunneling is another popular method for secure remote access. SSH tunneling encrypts data transmitted between the remote device and the internal network, providing an additional layer of security. This method is particularly useful for accessing specific services or applications behind a firewall.
Advantages of SSH tunneling include:
- Simple setup and configuration
- Support for multiple protocols and applications
- High level of security and encryption
While SSH tunneling is effective, it may not be suitable for large-scale deployments or complex network environments. Careful planning and testing are essential to ensure successful implementation.
Security Considerations
Security is a top priority when controlling devices behind firewalls. Ensuring secure connections and protecting sensitive data requires a multi-layered approach. Key security considerations include:
- Encryption: Use strong encryption protocols to protect data in transit.
- Authentication: Implement multi-factor authentication (MFA) to verify user identities.
- Access Control: Limit access to authorized users and devices only.
- Regular Updates: Keep software and firmware up to date to address vulnerabilities.
By adhering to these best practices, organizations can significantly reduce the risk of security breaches and unauthorized access.
Tools for Remote Control
Several tools and software solutions are available for remote control devices behind firewalls. Some popular options include:
- TeamViewer: A versatile tool for remote access and support, offering features such as file transfer and screen sharing.
- AnyDesk: A lightweight and efficient solution for remote control, with support for multiple platforms.
- Windows Remote Desktop: A built-in Windows feature for remote access, offering seamless integration with Microsoft products.
Each tool has its strengths and weaknesses, so selecting the right solution depends on specific requirements and use cases. Evaluating features, security, and compatibility is essential when choosing a remote control tool.
Implementing Remote Control Safely
Successfully implementing remote control devices behind firewalls requires careful planning and execution. Key steps include:
- Assessing Requirements: Identify the specific needs and goals of the remote access solution.
- Choosing the Right Tools: Select tools and technologies that align with organizational objectives.
- Configuring Firewalls: Adjust firewall settings to allow necessary connections while maintaining security.
- Testing and Validation: Conduct thorough testing to ensure functionality and security.
By following these steps, organizations can implement remote control solutions that are both effective and secure.
Best Practices for Remote Access
Adopting best practices is essential for maximizing the benefits of remote control devices behind firewalls. Some recommended practices include:
- Regular Audits: Conduct periodic security audits to identify and address vulnerabilities.
- Policy Development: Establish clear policies for remote access and enforce them consistently.
- User Training: Educate users on proper usage and security protocols to minimize risks.
- Monitoring and Logging: Implement monitoring and logging mechanisms to detect and respond to suspicious activities.
Implementing these best practices can help organizations maintain a secure and efficient remote access environment.
Future Trends in Remote Control Technology
The field of remote control technology is evolving rapidly, with new innovations and advancements emerging regularly. Some key trends to watch include:
- Artificial Intelligence (AI): AI-driven solutions for enhanced automation and efficiency.
- Cloud Computing: Increased adoption of cloud-based remote access solutions for scalability and flexibility.
- Quantum Encryption: Advances in quantum encryption for unparalleled security.
As technology continues to advance, staying informed about emerging trends and innovations will be crucial for organizations seeking to leverage remote control devices behind firewalls effectively.
Conclusion
Controlling devices behind firewalls is a critical capability in today's digital landscape. By understanding the challenges, solutions, and best practices involved, organizations can implement secure and efficient remote access solutions. From using VPNs and SSH tunneling to adopting advanced tools and technologies, there are numerous ways to enhance remote control capabilities while maintaining robust security.
We encourage readers to share their thoughts and experiences in the comments section below. Additionally, exploring related articles on our site can provide further insights into this fascinating and rapidly evolving field. Together, we can continue to advance the possibilities of remote control technology behind firewalls.