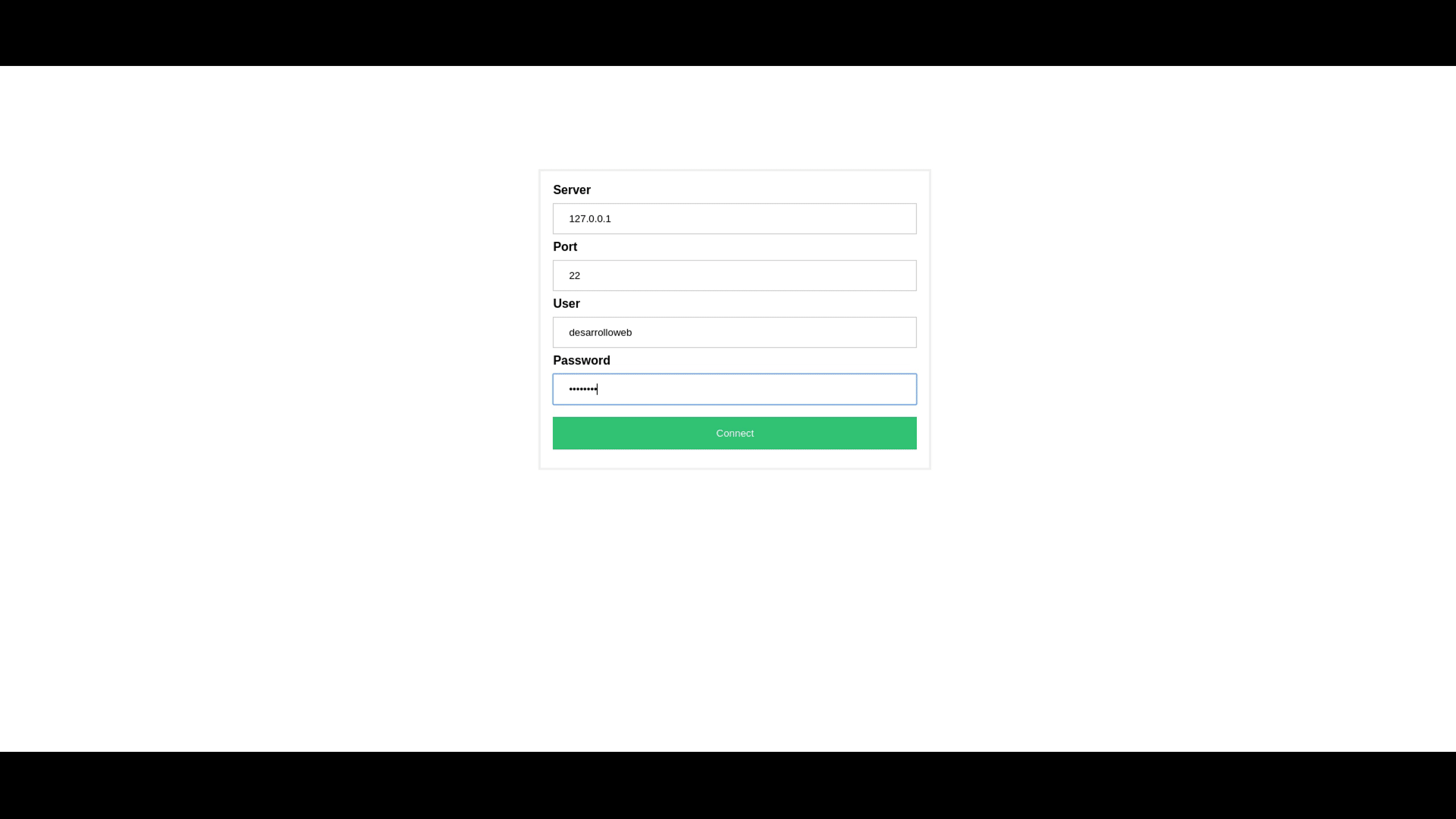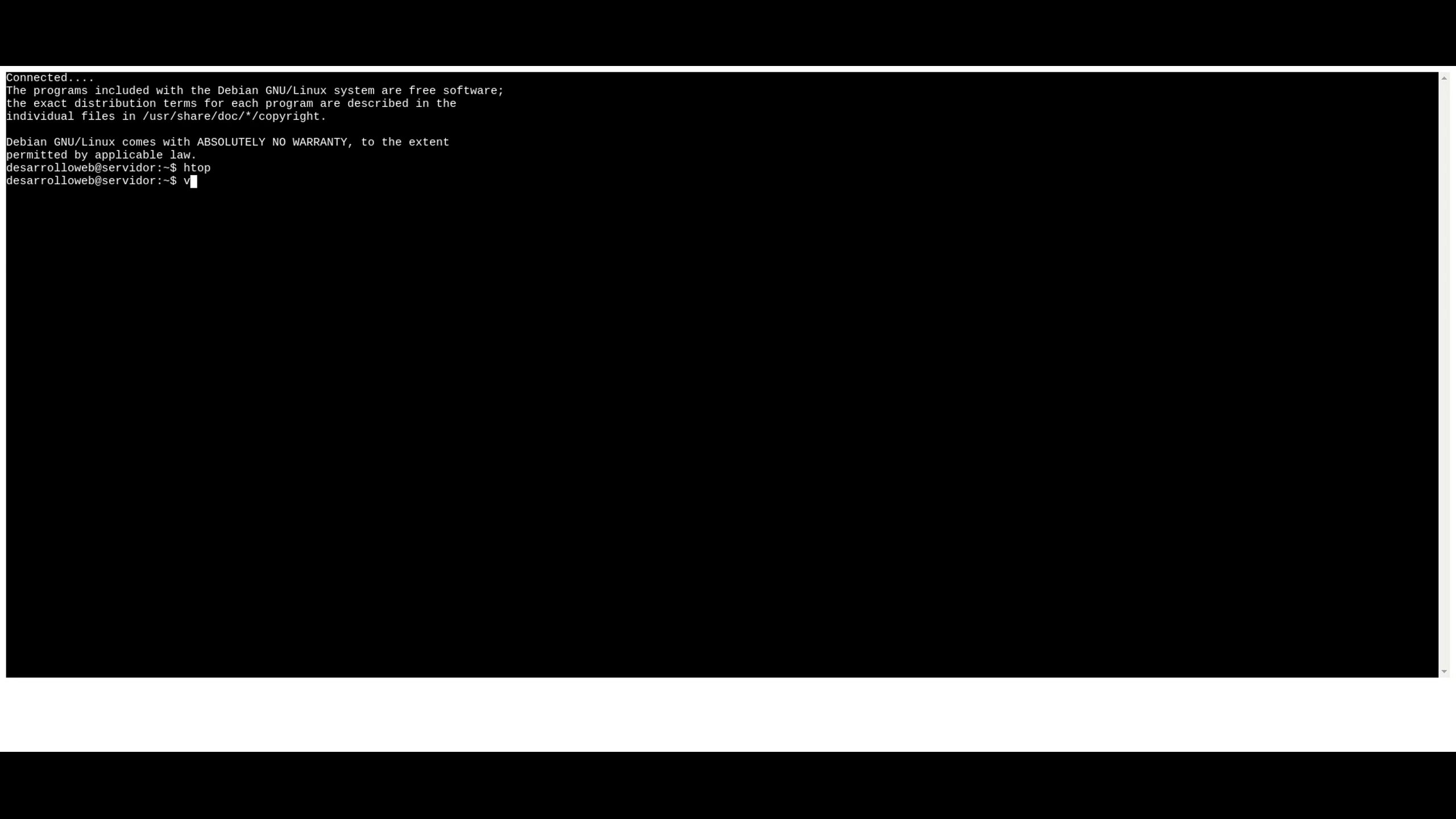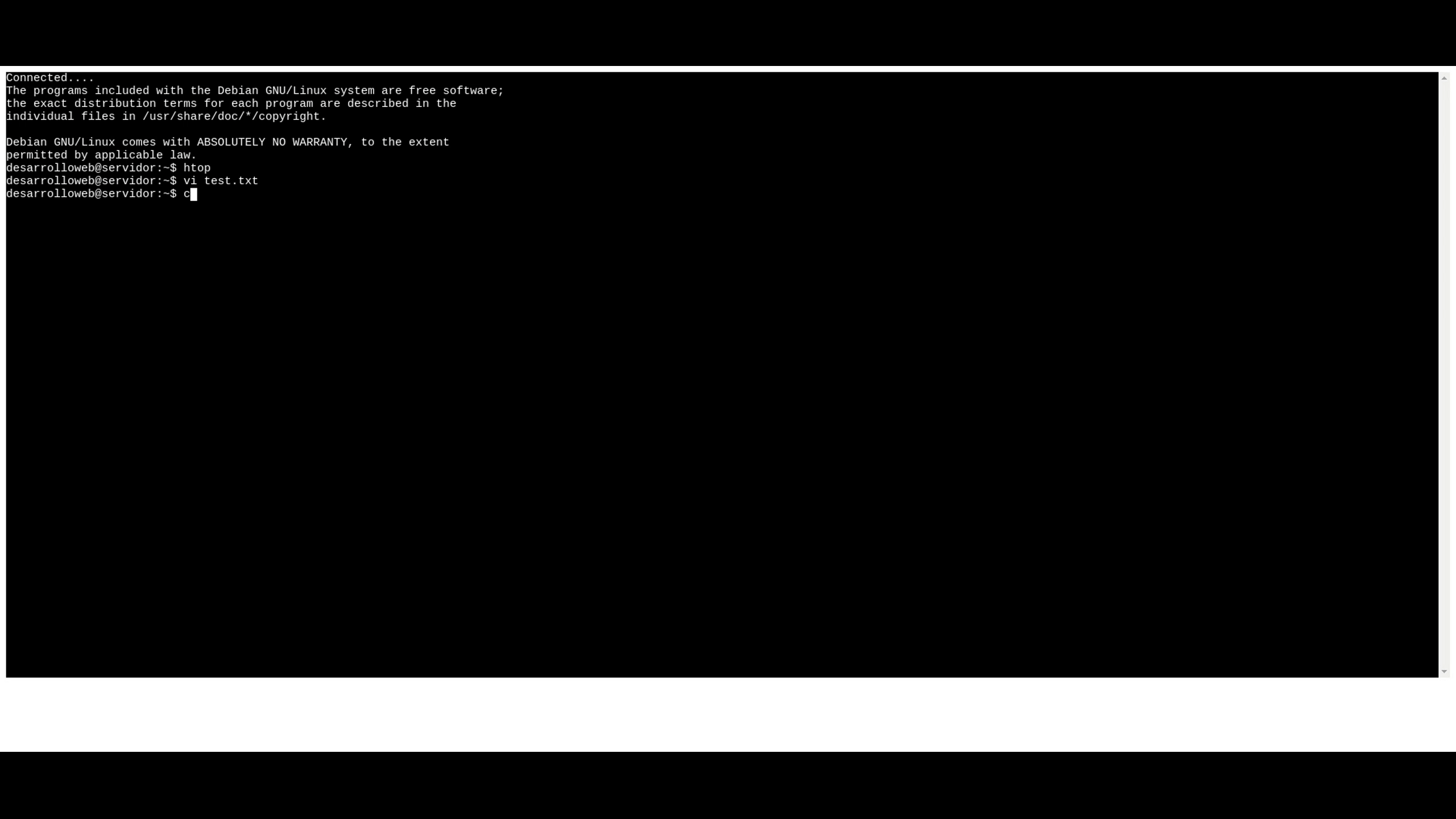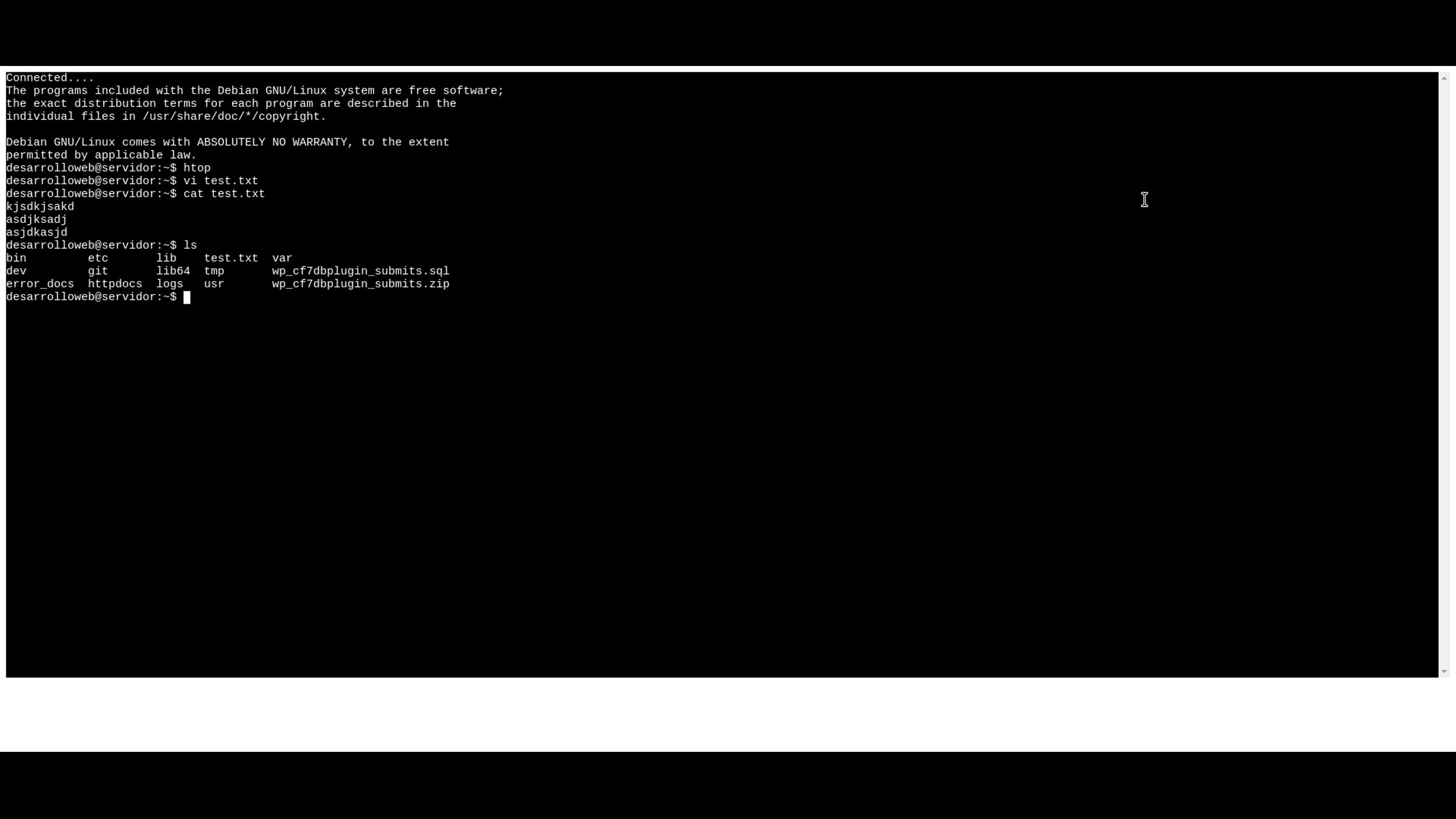
In today's digital age, remote IoT web SSH has become an essential tool for businesses and individuals seeking secure remote access to their devices and networks. As more organizations adopt IoT solutions, understanding and implementing secure access methods is crucial for safeguarding sensitive data and ensuring seamless connectivity.
With the increasing reliance on interconnected devices, the importance of secure remote access cannot be overstated. RemoteIoT web SSH provides a reliable solution for managing and monitoring IoT devices from anywhere in the world, enabling users to maintain control over their systems without compromising security.
This article will explore the concept of RemoteIoT web SSH, its benefits, challenges, and best practices for implementation. We'll also delve into the technical aspects of setting up and maintaining secure connections, ensuring that users can confidently adopt this technology in their operations.
Read also:How Tall Is Tobias Dorzon A Comprehensive Guide
Table of Contents
- Introduction to RemoteIoT Web SSH
- Key Benefits of Using RemoteIoT Web SSH
- How to Set Up RemoteIoT Web SSH
- Enhancing Security in RemoteIoT Web SSH
- Tools and Technologies for RemoteIoT Web SSH
- Common Challenges in RemoteIoT Web SSH
- Optimizing RemoteIoT Web SSH Performance
- Real-World Applications of RemoteIoT Web SSH
- The Future of RemoteIoT Web SSH
- Conclusion and Call to Action
Introduction to RemoteIoT Web SSH
RemoteIoT web SSH refers to the use of Secure Shell (SSH) protocols to establish secure, encrypted connections between IoT devices and remote users. This technology enables administrators and technicians to manage and monitor IoT devices from anywhere, ensuring that critical systems remain operational and secure.
The rise of IoT has transformed the way businesses operate, with millions of interconnected devices now deployed across various industries. RemoteIoT web SSH plays a vital role in this ecosystem by providing a secure and reliable method for remote access and management.
In this section, we'll discuss the fundamental principles of RemoteIoT web SSH, including its architecture, protocols, and key components. Understanding these basics is essential for anyone looking to implement this technology in their operations.
How SSH Works in IoT
SSH is a cryptographic network protocol designed to secure communication between devices over an unsecured network. In the context of IoT, SSH ensures that data transmitted between devices and remote users remains encrypted and protected from unauthorized access.
Key features of SSH in IoT include:
- Encryption of data in transit
- Authentication mechanisms for user verification
- Support for secure file transfers and command execution
Key Benefits of Using RemoteIoT Web SSH
Adopting RemoteIoT web SSH offers numerous advantages for businesses and individuals managing IoT devices. These benefits include enhanced security, improved efficiency, and greater flexibility in managing remote systems.
Read also:Unveiling The Truth About Boly4uin A Comprehensive Guide
By leveraging SSH protocols, users can ensure that their IoT devices remain secure and accessible from anywhere in the world. This capability is particularly valuable for organizations with distributed networks or those operating in remote locations.
Enhanced Security
One of the primary advantages of RemoteIoT web SSH is its ability to provide robust security features. By encrypting all data transmitted between devices and users, SSH minimizes the risk of unauthorized access and data breaches.
Additional security benefits include:
- Public key authentication for user verification
- Protection against man-in-the-middle attacks
- Compliance with industry standards and regulations
How to Set Up RemoteIoT Web SSH
Setting up RemoteIoT web SSH requires careful planning and execution to ensure that the system is secure and functional. This section will guide you through the process of configuring SSH for IoT devices, covering essential steps and best practices.
To begin, users must install and configure SSH software on their IoT devices. This typically involves enabling SSH services, generating public and private keys, and setting up user accounts with appropriate permissions.
Step-by-Step Guide
Follow these steps to set up RemoteIoT web SSH:
- Install SSH software on your IoT device
- Generate public and private keys for authentication
- Configure firewall settings to allow SSH traffic
- Test the connection to ensure proper functionality
Enhancing Security in RemoteIoT Web SSH
While RemoteIoT web SSH provides strong security features, additional measures can further enhance the protection of your IoT devices. This section will explore advanced security techniques and best practices for maintaining secure connections.
Implementing multi-factor authentication, regularly updating software, and monitoring system logs are just a few strategies that can help safeguard your IoT network from potential threats.
Best Practices for Security
Consider the following best practices to maximize security in RemoteIoT web SSH:
- Use strong passwords and avoid default credentials
- Regularly update SSH software and firmware
- Monitor system logs for suspicious activity
Tools and Technologies for RemoteIoT Web SSH
Several tools and technologies are available to assist with the implementation and management of RemoteIoT web SSH. These solutions can simplify the process of configuring and maintaining secure connections, making it easier for users to manage their IoT devices remotely.
Popular tools include OpenSSH, PuTTY, and SSH clients for various operating systems. These applications provide a user-friendly interface for establishing and managing SSH connections, ensuring that users can focus on their core tasks without worrying about technical details.
Choosing the Right Tools
When selecting tools for RemoteIoT web SSH, consider the following factors:
- Compatibility with your IoT devices and operating systems
- Ease of use and configuration
- Support for advanced security features
Common Challenges in RemoteIoT Web SSH
Despite its many advantages, RemoteIoT web SSH is not without its challenges. Issues such as network latency, bandwidth limitations, and compatibility problems can impact the performance and reliability of SSH connections.
In this section, we'll discuss common challenges associated with RemoteIoT web SSH and provide strategies for overcoming them. By addressing these issues proactively, users can ensure that their IoT systems remain secure and operational.
Strategies for Overcoming Challenges
To address common challenges in RemoteIoT web SSH, consider the following strategies:
- Optimize network configurations to reduce latency
- Implement load balancing and failover mechanisms
- Regularly test and evaluate system performance
Optimizing RemoteIoT Web SSH Performance
Maximizing the performance of RemoteIoT web SSH is essential for ensuring that users can access their IoT devices efficiently and effectively. This section will explore techniques for optimizing SSH connections, including network tuning, compression, and caching.
By implementing these strategies, users can improve the speed and reliability of their SSH connections, enabling seamless remote access to their IoT devices.
Performance Optimization Techniques
Consider the following techniques to optimize RemoteIoT web SSH performance:
- Enable compression for faster data transfer
- Tune network parameters for optimal performance
- Implement caching to reduce redundant data transmission
Real-World Applications of RemoteIoT Web SSH
RemoteIoT web SSH has numerous real-world applications across various industries, including manufacturing, healthcare, and transportation. In these sectors, secure remote access to IoT devices is critical for maintaining operational efficiency and ensuring data security.
This section will highlight specific use cases and examples of RemoteIoT web SSH in action, demonstrating its versatility and effectiveness in addressing modern business challenges.
Case Studies
Explore the following case studies to see how RemoteIoT web SSH is being used in practice:
- Remote monitoring of industrial equipment in manufacturing
- Secure access to medical devices in healthcare
- Real-time tracking of vehicles in transportation
The Future of RemoteIoT Web SSH
As IoT continues to evolve, the role of RemoteIoT web SSH will become increasingly important in ensuring secure and reliable remote access to interconnected devices. Advances in technology, such as quantum encryption and artificial intelligence, may further enhance the capabilities of SSH in the years to come.
This section will examine emerging trends and innovations in RemoteIoT web SSH, providing insights into the future of this critical technology.
Trends to Watch
Keep an eye on the following trends in RemoteIoT web SSH:
- Integration with AI and machine learning
- Adoption of quantum encryption for enhanced security
- Expansion into new industries and applications
Conclusion and Call to Action
In conclusion, RemoteIoT web SSH offers a powerful solution for secure remote access to IoT devices, enabling businesses and individuals to manage their systems efficiently and effectively. By understanding the principles, benefits, and challenges of this technology, users can confidently adopt RemoteIoT web SSH in their operations.
We invite you to take action by exploring the tools and resources mentioned in this article and implementing RemoteIoT web SSH in your own projects. Share your experiences and insights with our community by leaving a comment or reaching out via social media. Together, we can advance the field of IoT and secure remote access for the future.