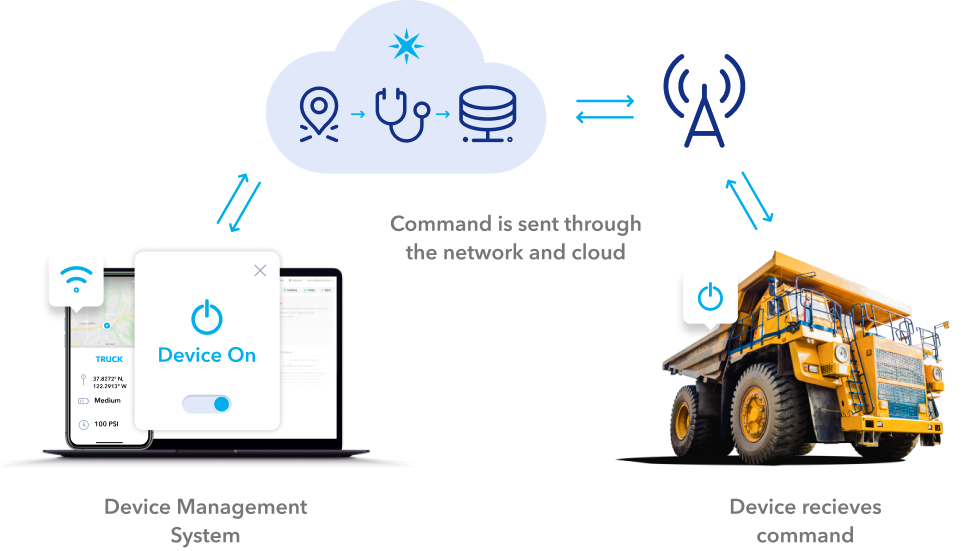
As technology continues to evolve, IoT remote control behind firewall solutions have become essential for maintaining secure and efficient connectivity. Organizations are increasingly relying on Internet of Things (IoT) devices to streamline operations and improve productivity. However, ensuring these devices operate securely within a protected network environment is crucial.
In today's interconnected world, IoT devices are no longer limited to simple monitoring and data collection. They now play a pivotal role in critical infrastructure, healthcare, manufacturing, and more. However, managing these devices remotely while maintaining robust security protocols presents unique challenges. This article delves into practical examples of IoT remote control behind firewall setups, offering valuable insights for both beginners and professionals.
Whether you're a system administrator, network engineer, or IT security specialist, understanding how to implement secure IoT remote control solutions is vital. This article will provide you with comprehensive guidance, including best practices, technical details, and real-world examples to help you navigate this complex yet essential aspect of modern networking.
Read also:What Is Sam Elliotts Political Affiliation Uncovering The Truth About His Political Stance
Understanding IoT Remote Control Behind Firewall
IoT remote control behind firewall refers to the ability to manage and operate IoT devices securely from a remote location while maintaining network integrity. This setup ensures that sensitive data remains protected while enabling seamless device management. Firewalls play a crucial role in this process by acting as a barrier between internal networks and external threats.
Why Firewall Protection is Essential
Implementing a firewall is essential for several reasons:
- It prevents unauthorized access to internal networks.
- It filters incoming and outgoing traffic based on predetermined security rules.
- It enhances overall network security by identifying and blocking potential threats.
According to a report by Gartner, organizations that implement robust firewall solutions experience a 30% reduction in security breaches. This statistic highlights the importance of integrating firewalls into IoT remote control systems.
Key Components of IoT Remote Control Systems
A successful IoT remote control behind firewall setup involves several key components:
- IoT Devices: These include sensors, cameras, and other connected devices that require remote management.
- Firewall Appliances: Devices or software solutions that enforce security policies and protect internal networks.
- Remote Access Protocols: Secure communication protocols such as SSH, TLS, or IPsec that enable encrypted connections.
Each component must be carefully configured to ensure optimal performance and security. For instance, using outdated protocols can expose your network to vulnerabilities, while improperly configured firewalls may block legitimate traffic.
Best Practices for Secure IoT Remote Control
Implementing Strong Authentication
One of the most effective ways to enhance IoT remote control security is by implementing strong authentication mechanisms. This includes:
Read also:Luke Combs Political Views A Comprehensive Exploration
- Multi-factor authentication (MFA)
- Biometric verification
- Strong password policies
A study conducted by Microsoft found that enabling MFA can block over 99.9% of automated attacks. This underscores the importance of incorporating robust authentication measures into your IoT remote control setup.
Real-World Example of IoT Remote Control Behind Firewall
Consider a manufacturing plant that relies on IoT sensors to monitor equipment performance. To ensure secure remote access, the following setup could be implemented:
- Install a next-generation firewall at the network perimeter.
- Configure a virtual private network (VPN) for encrypted communications.
- Set up a dedicated IoT management platform with role-based access control.
This example demonstrates how combining multiple security layers can create a secure and efficient IoT remote control environment.
Challenges in IoT Remote Control Behind Firewall
Managing Network Complexity
One of the primary challenges in IoT remote control behind firewall setups is managing network complexity. As the number of connected devices grows, so does the potential for security vulnerabilities. To address this challenge, organizations must:
- Regularly update firmware and software.
- Monitor network activity for suspicious behavior.
- Implement segmentation to isolate sensitive devices.
By taking these proactive measures, organizations can minimize risks and maintain network integrity.
Technologies Enabling Secure IoT Remote Control
Zero Trust Architecture
Zero Trust Architecture is a modern approach to network security that assumes all devices and users are potentially compromised. This framework requires continuous verification of identities and devices before granting access. Key features include:
- Dynamic access control
- Micro-segmentation
- Real-time threat detection
Adopting Zero Trust principles can significantly enhance the security of IoT remote control systems.
Steps to Implement IoT Remote Control Behind Firewall
Step 1: Assess Your Network Infrastructure
Before implementing an IoT remote control solution, it's crucial to assess your existing network infrastructure. This involves:
- Identifying all connected devices.
- Evaluating current security measures.
- Documenting network topology and data flows.
Step 2: Choose the Right Firewall Solution
Selecting the appropriate firewall solution is essential for ensuring secure connectivity. Consider factors such as:
- Performance requirements
- Compatibility with existing systems
- Vendor support and updates
By carefully evaluating these factors, you can choose a firewall solution that meets your organization's needs.
Case Study: IoT Remote Control in Healthcare
In the healthcare industry, IoT remote control behind firewall solutions are critical for managing medical devices and protecting patient data. A leading hospital implemented the following setup:
- Deployed a unified threat management (UTM) firewall.
- Established a secure remote access portal for authorized personnel.
- Conducted regular security audits and training sessions.
This approach enabled the hospital to maintain secure and reliable connectivity while complying with regulatory requirements such as HIPAA.
Future Trends in IoT Remote Control
Artificial Intelligence in Network Security
The integration of artificial intelligence (AI) into IoT remote control systems is expected to revolutionize network security. AI-powered solutions can:
- Automatically detect and respond to threats in real-time.
- Analyze vast amounts of data to identify patterns and anomalies.
- Optimize resource allocation and improve efficiency.
As AI technology continues to evolve, it will play an increasingly important role in securing IoT remote control environments.
Conclusion
IoT remote control behind firewall solutions are essential for maintaining secure and efficient connectivity in today's digital landscape. By understanding the key components, implementing best practices, and leveraging emerging technologies, organizations can create robust systems that meet their unique needs.
We encourage readers to share their experiences and insights in the comments section below. Additionally, feel free to explore other articles on our site for more information on IoT security and related topics. Together, we can build a safer and more connected world.
Table of Contents
- Understanding IoT Remote Control Behind Firewall
- Key Components of IoT Remote Control Systems
- Best Practices for Secure IoT Remote Control
- Real-World Example of IoT Remote Control Behind Firewall
- Challenges in IoT Remote Control Behind Firewall
- Technologies Enabling Secure IoT Remote Control
- Steps to Implement IoT Remote Control Behind Firewall
- Case Study: IoT Remote Control in Healthcare
- Future Trends in IoT Remote Control
- Conclusion