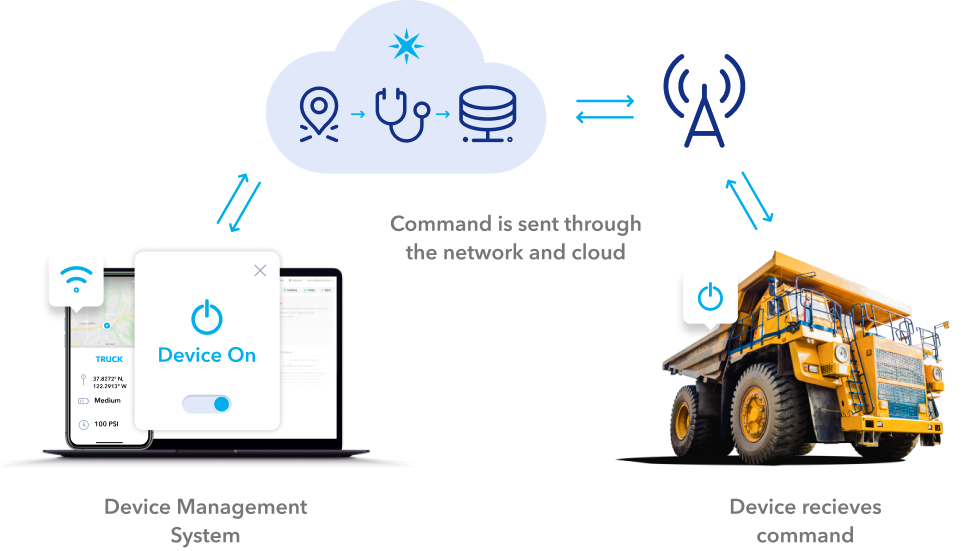
As the Internet of Things (IoT) continues to expand, the ability to remotely control IoT devices behind firewalls has become a critical topic for businesses and individuals alike. The convenience of remote access to IoT devices is undeniable, but it also raises significant security concerns. Understanding how to securely manage IoT remote control behind firewalls is essential for protecting sensitive data and maintaining system integrity.
IoT remote control behind firewall technology has revolutionized the way we interact with devices, whether it's monitoring home appliances, managing industrial equipment, or accessing office systems. However, the complexity of implementing secure remote control solutions can be overwhelming for those unfamiliar with networking and cybersecurity concepts.
In this article, we will explore the intricacies of IoT remote control behind firewalls, including the benefits, challenges, and best practices for ensuring secure communication. By the end of this guide, you will have a comprehensive understanding of how to implement and manage IoT remote control systems effectively.
Read also:Why Did Joe Leave Impractical Jokers The Untold Story
Table of Contents
- Introduction to IoT Remote Control Behind Firewall
- Benefits of IoT Remote Control Behind Firewall
- Security Challenges in IoT Remote Control
- Understanding Firewall Basics
- Methods for Remote Access Behind Firewalls
- Using VPN for IoT Remote Control
- Cloud-Based Solutions for IoT Remote Control
- Best Practices for Secure IoT Remote Control
- Emerging Technologies in IoT Remote Control
- Future Trends in IoT Remote Control
- Conclusion and Next Steps
Introduction to IoT Remote Control Behind Firewall
IoT remote control behind firewall refers to the ability to manage and interact with IoT devices located within a secure network from an external location. This functionality is crucial for modern businesses that rely on connected devices to monitor and manage operations remotely. By leveraging advanced networking technologies, organizations can ensure that their IoT devices remain accessible while maintaining robust security measures.
The primary goal of IoT remote control behind firewalls is to provide secure and reliable access to devices without compromising network security. Firewalls act as barriers that prevent unauthorized access to internal networks, making it essential to implement secure communication protocols for remote control purposes.
As the number of IoT devices continues to grow, the demand for secure remote control solutions has increased significantly. Businesses must adopt strategies that balance accessibility with security to protect their networks and data from potential threats.
Benefits of IoT Remote Control Behind Firewall
Enhanced Productivity
One of the most significant advantages of IoT remote control behind firewalls is the ability to improve productivity. By enabling remote access to devices, businesses can streamline operations and reduce the need for on-site interventions. This results in faster problem resolution and increased operational efficiency.
Cost Savings
Implementing IoT remote control solutions can lead to substantial cost savings. Instead of sending technicians to physical locations, organizations can troubleshoot and resolve issues remotely. This reduces travel expenses and minimizes downtime, allowing businesses to allocate resources more effectively.
Improved Security
With the right security measures in place, IoT remote control behind firewalls can enhance overall network security. By using secure communication protocols and encryption, businesses can protect sensitive data and prevent unauthorized access to their networks.
Read also:The Black Dahlia Autopsy A Gruesome Mystery That Still Haunts Us
Security Challenges in IoT Remote Control
While IoT remote control behind firewalls offers numerous benefits, it also presents several security challenges. One of the primary concerns is the potential for unauthorized access to internal networks. Hackers can exploit vulnerabilities in remote access systems to gain entry to sensitive data and disrupt operations.
- Weak authentication mechanisms
- Lack of encryption for data transmission
- Inadequate firewall configurations
- Unpatched software vulnerabilities
Addressing these challenges requires a comprehensive approach that combines robust security measures with regular system updates and monitoring.
Understanding Firewall Basics
Firewalls are essential components of network security, designed to protect internal systems from external threats. They act as gatekeepers, controlling incoming and outgoing traffic based on predefined rules and policies. When implementing IoT remote control behind firewalls, it is crucial to understand how firewalls function and how they can be configured to support secure communication.
There are several types of firewalls, including:
- Packet-filtering firewalls
- Stateful inspection firewalls
- Application-level gateways
- Next-generation firewalls
Each type of firewall offers unique features and capabilities, making it important to choose the right solution for your specific needs.
Methods for Remote Access Behind Firewalls
Port Forwarding
Port forwarding is a common method for enabling remote access to devices behind firewalls. This technique involves configuring the firewall to forward specific ports to internal devices, allowing external users to connect securely. While effective, port forwarding requires careful configuration to avoid exposing sensitive systems to potential threats.
SSH Tunneling
Secure Shell (SSH) tunneling provides a secure method for remote access by encrypting data transmitted between devices. This approach is particularly useful for managing IoT devices that require high levels of security. SSH tunneling can be combined with other security measures, such as two-factor authentication, to further enhance protection.
Reverse Proxies
Reverse proxies act as intermediaries between external users and internal devices, providing an additional layer of security for IoT remote control systems. By routing traffic through a reverse proxy, businesses can ensure that sensitive data remains protected from unauthorized access.
Using VPN for IoT Remote Control
Virtual Private Networks (VPNs) are widely used for secure remote access to IoT devices behind firewalls. By creating an encrypted tunnel between external users and internal networks, VPNs provide a secure and reliable method for managing IoT devices remotely. Organizations should consider implementing enterprise-grade VPN solutions to ensure the highest level of security.
Key benefits of using VPNs for IoT remote control include:
- Data encryption
- Authentication and authorization
- Network segmentation
- Scalability
Cloud-Based Solutions for IoT Remote Control
Cloud-based platforms offer innovative solutions for IoT remote control behind firewalls. By leveraging cloud infrastructure, businesses can centralize device management and streamline operations. Cloud-based solutions also provide enhanced security features, such as multi-factor authentication and real-time monitoring, to protect against potential threats.
Popular cloud-based platforms for IoT remote control include:
- Amazon Web Services (AWS) IoT
- Microsoft Azure IoT
- Google Cloud IoT
These platforms offer scalable and flexible solutions for managing IoT devices securely and efficiently.
Best Practices for Secure IoT Remote Control
Implement Strong Authentication Mechanisms
Using strong authentication mechanisms, such as two-factor authentication (2FA) and biometric verification, is essential for securing IoT remote control systems. These measures help ensure that only authorized users can access internal devices and networks.
Regularly Update Firmware and Software
Keeping firmware and software up to date is critical for maintaining the security of IoT devices. Regular updates address known vulnerabilities and improve overall system performance, reducing the risk of security breaches.
Monitor Network Activity
Implementing network monitoring tools allows businesses to detect and respond to suspicious activity in real time. This proactive approach helps prevent unauthorized access and minimizes the impact of potential security incidents.
Emerging Technologies in IoT Remote Control
The field of IoT remote control is rapidly evolving, with new technologies and innovations emerging regularly. Some of the most promising developments include:
- Blockchain for secure device management
- Artificial intelligence for predictive maintenance
- Edge computing for improved performance
These technologies have the potential to transform the way businesses manage IoT devices, offering enhanced security and efficiency.
Future Trends in IoT Remote Control
As the IoT ecosystem continues to expand, several trends are expected to shape the future of remote control behind firewalls. These include increased adoption of cloud-based solutions, greater emphasis on cybersecurity, and the integration of emerging technologies like 5G and quantum computing.
Businesses that stay ahead of these trends will be better positioned to capitalize on the opportunities presented by IoT remote control while mitigating potential risks.
Conclusion and Next Steps
In conclusion, IoT remote control behind firewalls is a critical component of modern network management. By understanding the benefits, challenges, and best practices associated with this technology, businesses can implement secure and effective solutions for managing IoT devices remotely.
We encourage readers to take the following steps:
- Review your current IoT remote control setup and identify areas for improvement
- Implement best practices for secure communication and authentication
- Explore emerging technologies and trends in IoT remote control
- Share your thoughts and experiences in the comments section below
Thank you for reading this comprehensive guide on IoT remote control behind firewalls. We hope you found it informative and useful. For more insights and updates on IoT technology, be sure to explore our other articles and resources.