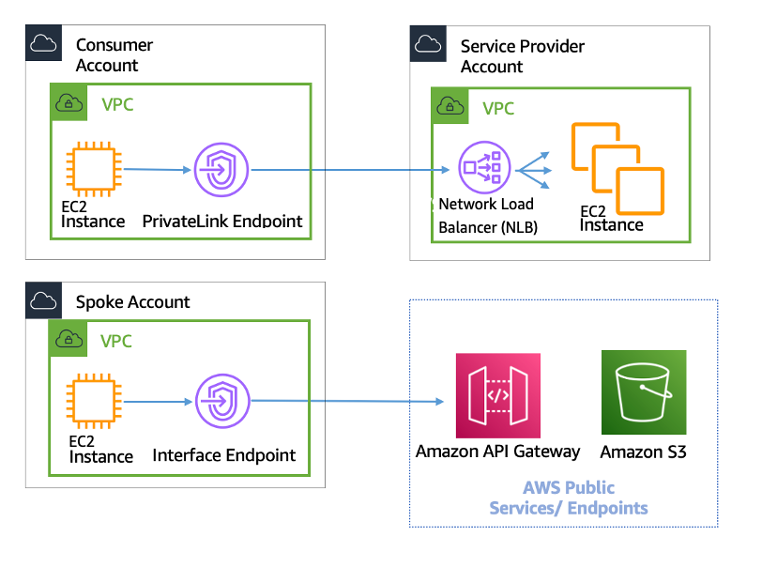
Connecting remote IoT devices to a Virtual Private Cloud (VPC) on AWS securely is a critical step in ensuring robust communication and protecting sensitive data. As more organizations adopt IoT solutions, the need for secure and scalable connectivity grows exponentially. This article will explore the best practices, tools, and strategies to achieve secure remote IoT VPC connections on AWS. Whether you're a developer, system administrator, or IT professional, understanding how to implement secure connections is essential for maintaining the integrity of your IoT ecosystem.
With the increasing reliance on cloud computing and IoT devices, securing these connections has become a top priority. AWS provides a wide range of tools and services that allow users to create secure and efficient communication channels between IoT devices and their VPCs. By leveraging AWS's robust infrastructure, organizations can ensure that their IoT devices operate seamlessly while maintaining the highest levels of security.
This guide will cover everything you need to know about securely connecting remote IoT devices to a VPC on AWS. From setting up VPCs and configuring security groups to implementing encryption and monitoring tools, this article will provide actionable insights and practical tips to help you secure your IoT ecosystem.
Read also:Who Is Adam Schiff Married To Discovering The Personal Life Of A Prominent Political Figure
Table of Contents
- Introduction to Secure IoT VPC Connections
- Understanding AWS VPC
- What is IoT and Why Security Matters?
- Setting Up Your VPC
- Configuring Security Groups
- Implementing Encryption for Secure Connections
- Managing Network ACLs
- Enabling Secure Remote Access
- Monitoring and Logging for Enhanced Security
- Best Practices for Securing IoT VPC Connections
- Conclusion and Next Steps
Introduction to Secure IoT VPC Connections
Securely connect remote IoT VPC on AWS is a fundamental aspect of modern cloud-based IoT deployments. The Internet of Things (IoT) has revolutionized the way we interact with technology, enabling devices to communicate and exchange data seamlessly. However, this increased connectivity also introduces significant security challenges. Organizations must ensure that their IoT devices are securely connected to their VPCs to prevent unauthorized access and data breaches.
AWS offers a comprehensive suite of tools and services to facilitate secure IoT VPC connections. By leveraging these tools, organizations can create a secure and scalable environment for their IoT devices. This section will explore the importance of secure connections and how AWS can help organizations achieve this goal.
Understanding AWS VPC
Amazon Virtual Private Cloud (VPC) is a service that allows users to create an isolated section of the AWS cloud where they can launch resources in a virtual network. A VPC provides a secure and flexible environment for deploying applications and services. By default, a VPC is isolated from other networks, ensuring that only authorized traffic can access its resources.
Key Features of AWS VPC
- Private Subnets: Allows users to create private subnets that are not accessible from the internet.
- Security Groups: Acts as a virtual firewall for controlling inbound and outbound traffic.
- Network Access Control Lists (ACLs): Provides an additional layer of security by controlling traffic at the subnet level.
- IP Address Management: Enables users to define their own IP address ranges and manage them efficiently.
What is IoT and Why Security Matters?
The Internet of Things (IoT) refers to the network of physical devices embedded with sensors, software, and connectivity that allows them to exchange data. IoT devices range from simple sensors to complex industrial machinery. As the number of IoT devices continues to grow, so does the need for robust security measures.
Securing IoT devices is critical because they often handle sensitive data and can serve as entry points for cyberattacks. A breach in one device can compromise the entire network, leading to significant financial and reputational damage. Therefore, ensuring secure connections between IoT devices and VPCs is essential for maintaining the integrity of the IoT ecosystem.
Setting Up Your VPC
Setting up a VPC on AWS involves several steps, including defining the IP address range, creating subnets, and configuring routing tables. Properly configuring your VPC ensures that it can securely accommodate your IoT devices and applications.
Read also:Randy Travis And Aphasia A Journey Through Challenges And Triumphs
Steps to Set Up a VPC
- Create a VPC with a custom IP address range.
- Define public and private subnets for your resources.
- Set up routing tables to control traffic flow between subnets.
- Configure internet gateways for public subnets.
Configuring Security Groups
Security groups act as virtual firewalls for controlling inbound and outbound traffic to your VPC resources. Properly configuring security groups is essential for ensuring secure connections between IoT devices and your VPC.
Best Practices for Security Groups
- Use specific IP ranges instead of allowing all traffic.
- Limit access to only necessary ports and protocols.
- Regularly review and update security group rules to reflect changing requirements.
Implementing Encryption for Secure Connections
Encryption is a critical component of securing IoT VPC connections on AWS. By encrypting data in transit and at rest, organizations can protect sensitive information from unauthorized access. AWS provides several encryption options, including SSL/TLS for securing communications and AWS KMS for managing encryption keys.
Encryption Tools on AWS
- SSL/TLS: Encrypts data in transit between IoT devices and VPCs.
- AWS KMS: Manages encryption keys for data at rest.
- Amazon S3 Encryption: Protects data stored in S3 buckets.
Managing Network ACLs
Network Access Control Lists (ACLs) provide an additional layer of security by controlling traffic at the subnet level. While security groups control traffic at the instance level, network ACLs offer more granular control over traffic entering and leaving subnets.
Configuring Network ACLs
- Define rules for allowing or denying traffic based on IP address, port, and protocol.
- Set up logging to monitor and analyze traffic patterns.
- Regularly review and update ACL rules to ensure they align with your security policies.
Enabling Secure Remote Access
Enabling secure remote access to your VPC is essential for managing IoT devices and applications. AWS provides several tools for facilitating secure remote access, including AWS Direct Connect and AWS Site-to-Site VPN.
Remote Access Options
- AWS Direct Connect: Provides a dedicated network connection between your on-premises infrastructure and AWS.
- AWS Site-to-Site VPN: Establishes a secure connection between your VPC and remote networks.
- AWS Client VPN: Allows individual users to securely access your VPC resources.
Monitoring and Logging for Enhanced Security
Monitoring and logging are critical components of securing IoT VPC connections on AWS. By monitoring traffic and analyzing logs, organizations can detect and respond to potential security threats in real time. AWS provides several tools for monitoring and logging, including Amazon CloudWatch and AWS CloudTrail.
Monitoring Tools on AWS
- Amazon CloudWatch: Monitors metrics and logs for your AWS resources.
- AWS CloudTrail: Tracks API calls and user activity within your AWS account.
- AWS Shield: Protects against DDoS attacks and other malicious activities.
Best Practices for Securing IoT VPC Connections
Implementing best practices for securing IoT VPC connections on AWS can significantly enhance the security of your IoT ecosystem. Here are some key recommendations:
Key Best Practices
- Regularly update and patch your IoT devices and applications.
- Implement multi-factor authentication for accessing VPC resources.
- Conduct regular security audits and vulnerability assessments.
- Limit access to VPC resources to only authorized personnel.
Conclusion and Next Steps
Securing remote IoT VPC connections on AWS is a critical step in ensuring the integrity and reliability of your IoT ecosystem. By following the best practices and utilizing the tools and services provided by AWS, organizations can create a secure and scalable environment for their IoT devices. Remember to regularly review and update your security policies to stay ahead of emerging threats.
We encourage you to take action by implementing the strategies discussed in this article. Leave a comment below to share your thoughts or ask questions. Don't forget to explore other articles on our website for more insights into AWS and IoT security.