In today's interconnected world, securely connect remote IoT P2P Raspberry Pi download Mac free has become a crucial topic for tech enthusiasts and professionals alike. As more devices join the Internet of Things (IoT) ecosystem, ensuring secure communication and data transfer is paramount. This guide will walk you through the steps to establish a secure connection for your Raspberry Pi-based IoT projects while keeping costs low.
This article delves into the intricacies of setting up a peer-to-peer (P2P) connection for your Raspberry Pi, ensuring it remains secure and accessible remotely. Whether you're a beginner or an experienced developer, this guide provides valuable insights into creating a robust IoT setup without spending a dime on proprietary software.
By the end of this article, you'll have a clear understanding of how to download and configure your Raspberry Pi for remote IoT P2P connectivity, all while maintaining security and compatibility with macOS systems. Let's dive in!
Read also:Martha Maccallum Age A Comprehensive Look At The Renowned Journalistrsquos Life And Career
Table of Contents
- Introduction to Secure IoT Connections
- Understanding Raspberry Pi Basics
- Essentials of IoT and P2P Connectivity
- Security Considerations for IoT Devices
- Setting Up Remote Access for Raspberry Pi
- Ensuring Compatibility with macOS
- Free Solutions for Secure IoT Connections
- Best Practices for Secure Connections
- Troubleshooting Common Issues
- Conclusion and Next Steps
Introduction to Secure IoT Connections
Why Security Matters in IoT
As the Internet of Things continues to expand, the need for secure connections becomes increasingly critical. Devices connected to the IoT network are often vulnerable to cyber threats, making it essential to implement robust security measures. When you securely connect remote IoT P2P Raspberry Pi, you ensure that your data remains protected and your devices function reliably.
Peer-to-peer (P2P) connectivity offers a decentralized approach to networking, reducing reliance on centralized servers and enhancing security. By leveraging P2P technology, you can establish a secure and efficient connection between devices, even when they are geographically distant.
Understanding Raspberry Pi Basics
What is Raspberry Pi?
The Raspberry Pi is a compact, affordable single-board computer designed for educational and DIY projects. It has become a popular choice for IoT enthusiasts due to its versatility and ease of use. With its GPIO pins and support for multiple operating systems, the Raspberry Pi serves as an ideal platform for developing secure IoT applications.
Key features of the Raspberry Pi include:
- Compact size and low power consumption
- Support for multiple programming languages
- Compatibility with various peripherals
- Open-source community support
Essentials of IoT and P2P Connectivity
Understanding IoT Architecture
The Internet of Things (IoT) architecture typically consists of three layers: the perception layer, the network layer, and the application layer. Each layer plays a vital role in enabling devices to communicate and exchange data.
P2P connectivity simplifies the network layer by allowing devices to communicate directly without the need for intermediaries. This reduces latency and improves overall performance, making it an attractive option for IoT applications.
Read also:Jesse Martin The Remarkable Story Of A Young Sailor Who Circumnavigated The Globe
Security Considerations for IoT Devices
Common IoT Security Threats
IoT devices are susceptible to various security threats, including:
- Data breaches
- Denial-of-service (DoS) attacks
- Malware infections
- Unauthorized access
To securely connect remote IoT P2P Raspberry Pi, it's crucial to implement measures such as encryption, authentication, and regular firmware updates. These practices help mitigate potential risks and ensure the longevity of your IoT setup.
Setting Up Remote Access for Raspberry Pi
Configuring SSH for Secure Access
Secure Shell (SSH) is a protocol that enables secure remote access to your Raspberry Pi. To set up SSH, follow these steps:
- Enable SSH in the Raspberry Pi configuration settings
- Generate SSH keys for authentication
- Set up port forwarding on your router
- Use an SSH client to connect remotely
By configuring SSH, you can securely connect remote IoT P2P Raspberry Pi from anywhere in the world, ensuring your data remains protected during transmission.
Ensuring Compatibility with macOS
Connecting Raspberry Pi to macOS
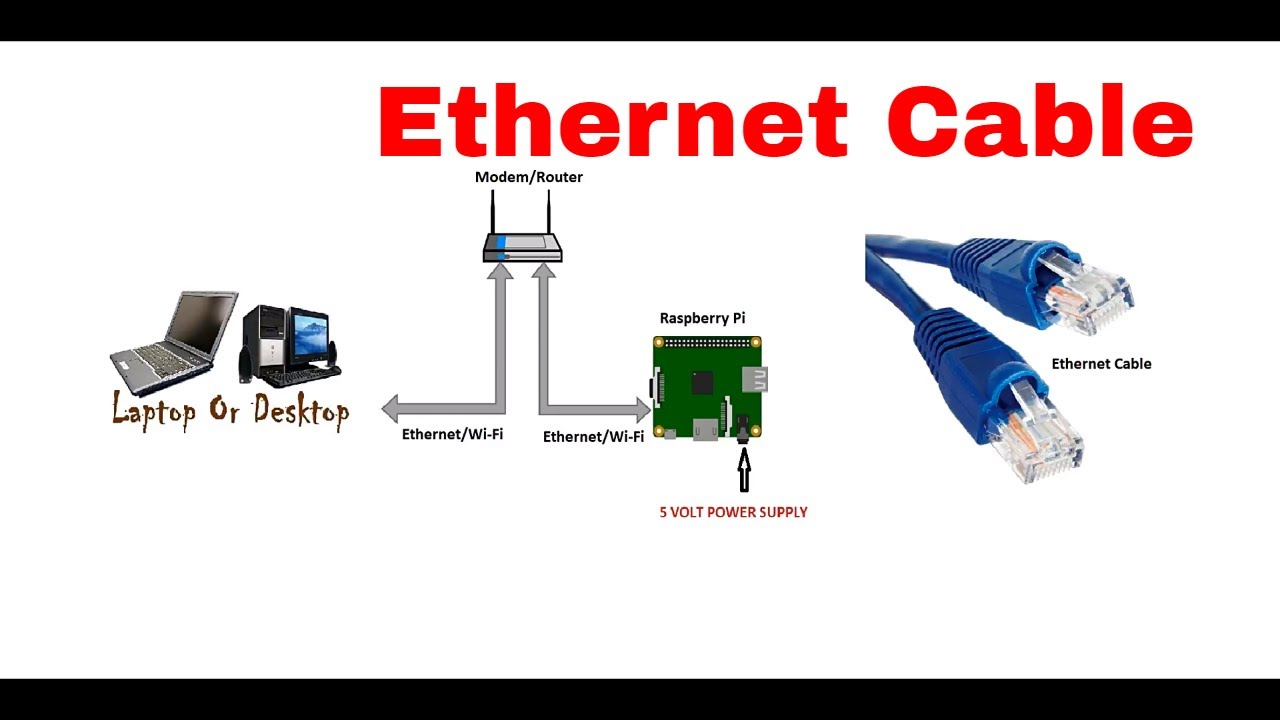
Mac users can easily connect their Raspberry Pi devices by leveraging built-in tools such as Terminal and Finder. To establish a connection:
- Install the necessary drivers and software
- Connect the Raspberry Pi to your Mac via Ethernet or Wi-Fi
- Use SSH or VNC for remote access
This setup allows you to securely connect remote IoT P2P Raspberry Pi download Mac free, providing seamless integration between your devices.
Free Solutions for Secure IoT Connections
Open-Source Tools for IoT Security
Several free and open-source tools are available to enhance the security of your IoT setup. Some popular options include:
- OpenVPN for secure tunneling
- Fail2Ban for intrusion prevention
- ClamAV for malware detection
By incorporating these tools into your Raspberry Pi configuration, you can create a secure and reliable IoT environment without incurring additional costs.
Best Practices for Secure Connections
Implementing Strong Authentication
Strong authentication mechanisms are essential for securing your IoT devices. Consider implementing the following practices:
- Use strong, unique passwords for all accounts
- Enable two-factor authentication (2FA) wherever possible
- Regularly update firmware and software
- Limit access to trusted devices and networks
Following these best practices ensures that your Raspberry Pi-based IoT projects remain secure and resilient against potential threats.
Troubleshooting Common Issues
Resolving Connectivity Problems
Encountering connectivity issues when securely connecting remote IoT P2P Raspberry Pi is not uncommon. To troubleshoot these problems:
- Verify network settings and IP configurations
- Check firewall rules and port forwarding settings
- Test the connection using diagnostic tools
- Consult online forums and community resources
By systematically addressing these issues, you can restore functionality and maintain a secure connection for your IoT devices.
Conclusion and Next Steps
In conclusion, securely connecting remote IoT P2P Raspberry Pi download Mac free is an achievable goal with the right tools and knowledge. By following the steps outlined in this guide, you can create a robust and secure IoT setup that meets your needs and ensures the safety of your data.
We encourage you to share your experiences and insights in the comments below. Additionally, explore other articles on our site for more information on IoT security and Raspberry Pi projects. Together, let's build a safer and more connected future!
Data Sources: