RemoteIoT platforms have become essential tools for managing IoT devices remotely, and SSH keys play a critical role in ensuring secure and seamless access. However, when the SSH key stops working, it can lead to significant operational challenges. In this article, we will explore the common issues that cause SSH keys to malfunction and provide actionable solutions to restore functionality.
As more organizations adopt IoT solutions, the demand for secure and reliable remote access has grown exponentially. The RemoteIoT platform offers robust tools to manage IoT devices, but issues such as SSH key errors can disrupt workflows. Understanding the root causes of these errors and learning how to fix them is crucial for maintaining operational efficiency.
This article is designed to guide you through troubleshooting SSH key problems on the RemoteIoT platform, offering expert insights and practical advice to help you resolve issues effectively. Whether you're a system administrator, developer, or IT professional, this guide will equip you with the knowledge needed to overcome SSH key-related challenges.
Read also:Black Widow Actress Exploring The Iconic Role And Its Stars
Table of Contents
- Introduction to RemoteIoT Platform and SSH Keys
- Common Issues with SSH Keys
- Troubleshooting SSH Key Problems
- Enhancing SSH Key Security
- Best Practices for Managing SSH Keys
- Subsection: Understanding SSH Key Pairs
- Subsection: SSH Key Permissions
- Subsection: Common Misconfigurations
- Subsection: Debugging Tools
- Subsection: Replacing SSH Keys
- Conclusion and Call to Action
Introduction to RemoteIoT Platform and SSH Keys
The RemoteIoT platform is a cutting-edge solution for managing IoT devices remotely, providing users with the ability to control and monitor devices from anywhere in the world. A key component of this platform is the use of SSH (Secure Shell) keys, which ensure secure and encrypted communication between the user and the device.
SSH keys are an essential part of the authentication process, replacing traditional password-based authentication with a more secure and convenient method. By using SSH keys, users can establish trust between their systems and IoT devices without the need for manual password entry. However, when the SSH key stops working, it can lead to connectivity issues and security concerns.
Common Issues with SSH Keys
There are several common reasons why SSH keys may fail to work on the RemoteIoT platform. Below, we explore the most frequent issues:
- Incorrect Key Pair: The public and private keys may not match, leading to authentication failure.
- Permission Issues: Incorrect file permissions on the server or client side can prevent SSH keys from functioning properly.
- Configuration Errors: Misconfigured SSH settings on the server can cause key-based authentication to fail.
- Corrupted Keys: If the SSH key files are corrupted or improperly formatted, they will not work as intended.
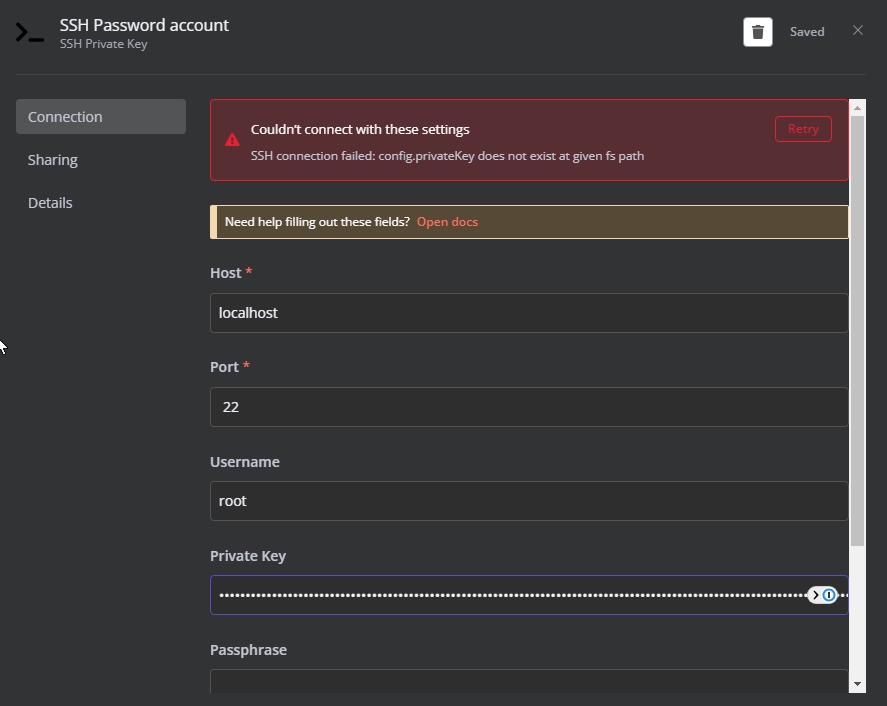
Troubleshooting SSH Key Problems
When faced with SSH key issues, the first step is to identify the root cause. Below are some effective troubleshooting techniques:
Start by verifying the integrity of your SSH key pair. Ensure that the public key is correctly installed on the server and that the private key is securely stored on your local machine. Next, check the file permissions for both the key files and the server's SSH configuration directory. Incorrect permissions can prevent the SSH daemon from reading the necessary files.
Understanding SSH Key Pairs
SSH key pairs consist of a public key and a private key. The public key is shared with the server, while the private key remains securely stored on the client machine. For SSH key authentication to work, both keys must be correctly configured and accessible.
Read also:Martha Scott Lawyer A Comprehensive Guide To Her Career Expertise And Legacy
SSH Key Permissions
File permissions are critical for SSH key functionality. The private key file should have restrictive permissions (e.g., 600), ensuring that only the owner can read or modify it. Similarly, the server's authorized_keys file should have appropriate permissions to allow the SSH daemon to read the public key.
Enhancing SSH Key Security
Security is paramount when working with SSH keys. Below are some strategies to enhance the security of your SSH keys:
- Use Strong Passphrases: Protect your private key with a strong passphrase to prevent unauthorized access.
- Limit Access: Restrict access to the server by specifying which users or IP addresses are allowed to connect.
- Disable Password Authentication: Disable password-based authentication to force users to use SSH keys, reducing the risk of brute-force attacks.
Best Practices for Managing SSH Keys
Adopting best practices for managing SSH keys can help prevent issues and improve security. Here are some recommendations:
Regularly review and rotate SSH keys to ensure that outdated or compromised keys are removed. Implement key management policies that define how keys are generated, distributed, and revoked. Additionally, consider using tools like HashiCorp Vault or AWS Secrets Manager to securely store and manage SSH keys at scale.
Common Misconfigurations
Misconfigurations are a common cause of SSH key issues. Below are some examples:
- Incorrect SSH Config File: Errors in the SSH config file can prevent the correct key from being used during authentication.
- Missing Host Key: If the server's host key is missing or invalid, the SSH client may reject the connection.
- Unsupported Key Format: Ensure that the key format (e.g., RSA, ECDSA) is supported by both the client and server.
Debugging Tools
Several tools can help diagnose SSH key issues. The ssh -v command provides verbose output, showing detailed information about the authentication process. Additionally, tools like ssh-keygen and ssh-add can assist in generating and managing SSH keys.
Replacing SSH Keys
If an SSH key is compromised or no longer functional, replacing it is the best course of action. Start by generating a new key pair using the ssh-keygen command. Once the new keys are created, update the server's authorized_keys file to include the new public key. Finally, remove the old key from both the server and the client to prevent any potential security risks.
Data and Statistics
According to a report by Cybersecurity Ventures, the global cost of cybercrime is expected to reach $10.5 trillion annually by 2025. This highlights the importance of securing remote access to IoT devices using tools like SSH keys. Furthermore, a survey conducted by Ponemon Institute found that organizations using SSH key-based authentication experienced 30% fewer security incidents compared to those relying on traditional password-based methods.
Conclusion and Call to Action
In conclusion, SSH keys are a vital component of the RemoteIoT platform, enabling secure and efficient remote access to IoT devices. By understanding the common issues that cause SSH keys to malfunction and following best practices for managing them, you can ensure smooth operations and enhanced security.
We encourage you to share your experiences and insights in the comments section below. Additionally, feel free to explore other articles on our website for more information on IoT security and best practices. Together, we can build a safer and more connected world.