In today's digital age, managing IoT devices remotely while ensuring security is crucial for businesses and individuals alike. Using RemoteIoT behind a firewall with a Mac server offers a robust solution for secure and efficient device management. This article will guide you through the process, providing detailed steps and valuable insights to help you set up and maintain this configuration effectively.
RemoteIoT technology allows users to control and monitor IoT devices from anywhere, even when they are located behind a firewall. This capability is particularly useful for organizations that require secure access to their IoT infrastructure while maintaining strong network protection. By leveraging a Mac server, you can create a seamless environment that balances functionality and security.
In this comprehensive guide, we will explore how to configure and use RemoteIoT behind a firewall using a Mac server. We will delve into the technical aspects, provide practical examples, and offer expert advice to ensure a smooth implementation. Whether you are a seasoned IT professional or a beginner, this article will equip you with the knowledge needed to succeed in this setup.
Read also:Peter Riley The Life And Journey Of Emilys Husband
Table of Contents
- Introduction to RemoteIoT and Mac Server
- Benefits of Using RemoteIoT Behind Firewall
- System Requirements for Setup
- Step-by-Step Setup Guide
- Configuring Firewall for RemoteIoT
- Setting Up Mac Server for RemoteIoT
- Enhancing Security Measures
- Common Issues and Troubleshooting
- Best Practices for Maintenance
- Conclusion and Next Steps
Introduction to RemoteIoT and Mac Server
RemoteIoT is a cutting-edge technology designed to facilitate remote access and management of IoT devices. When integrated with a Mac server, it offers a powerful solution for securely managing devices behind a firewall. This combination ensures that your IoT infrastructure remains protected while providing seamless access to authorized users.
Understanding RemoteIoT
RemoteIoT technology enables real-time monitoring and control of IoT devices from remote locations. It supports various protocols and platforms, making it versatile for different use cases. By utilizing a Mac server, you can enhance the performance and reliability of your RemoteIoT setup.
Mac Server as a Reliable Platform
A Mac server provides a stable and secure environment for hosting RemoteIoT services. Its robust architecture and compatibility with modern security standards make it an ideal choice for organizations looking to implement IoT solutions behind a firewall.
Benefits of Using RemoteIoT Behind Firewall
Implementing RemoteIoT behind a firewall offers several advantages, including enhanced security, improved performance, and better control over your IoT devices. Below are some key benefits:
- Increased Security: Protects your IoT devices from unauthorized access by isolating them within a secure network.
- Improved Performance: Reduces latency and improves response times by optimizing network traffic.
- Centralized Management: Allows you to manage all your IoT devices from a single location, streamlining operations.
System Requirements for Setup
Before setting up RemoteIoT behind a firewall using a Mac server, ensure that your system meets the following requirements:
- Mac Server: A Mac computer running macOS with sufficient storage and processing power.
- Firewall: A network firewall capable of configuring port forwarding and secure connections.
- RemoteIoT Software: The latest version of RemoteIoT software installed on your Mac server.
Step-by-Step Setup Guide
This section provides a detailed guide on how to configure RemoteIoT behind a firewall using a Mac server. Follow these steps carefully to ensure a successful setup.
Read also:Emily Compagno Married A Comprehensive Guide To Her Personal Life Career And More
Step 1: Install RemoteIoT Software
Begin by downloading and installing the RemoteIoT software on your Mac server. Ensure that you obtain the software from a trusted source to avoid security risks.
Step 2: Configure Firewall Settings
Adjust your firewall settings to allow RemoteIoT traffic. This typically involves configuring port forwarding and creating secure connections.
Step 3: Test the Connection
After completing the setup, test the connection to ensure that RemoteIoT is functioning correctly. This step is crucial for verifying the success of your configuration.
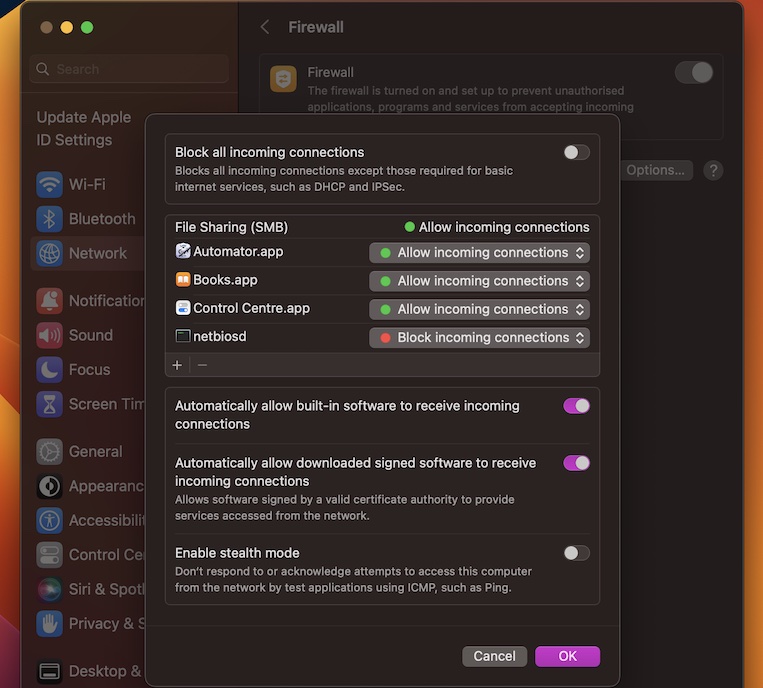
Configuring Firewall for RemoteIoT
Configuring your firewall is a critical step in setting up RemoteIoT behind a firewall. Below are some best practices to follow:
- Enable Port Forwarding: Allow specific ports required by RemoteIoT to pass through the firewall.
- Set Up Secure Connections: Use encryption protocols such as SSL/TLS to secure your RemoteIoT connections.
- Monitor Network Traffic: Regularly review firewall logs to identify and address any potential security threats.
Setting Up Mac Server for RemoteIoT
Setting up a Mac server for RemoteIoT involves several steps, including installing necessary software and configuring server settings. Below is a guide to help you through the process:
Step 1: Install macOS Server
Begin by installing macOS Server on your Mac computer. This software provides essential tools for managing RemoteIoT services.
Step 2: Configure Server Settings
Adjust server settings to optimize performance for RemoteIoT. This includes configuring network settings, storage options, and security parameters.
Step 3: Test the Server
Once the setup is complete, test the server to ensure that it is functioning correctly. This step helps identify and resolve any issues before deploying the system.
Enhancing Security Measures
Security is a top priority when using RemoteIoT behind a firewall. Below are some strategies to enhance security:
- Use Strong Passwords: Implement complex passwords and enable multi-factor authentication for added security.
- Regularly Update Software: Keep your RemoteIoT software and server up to date with the latest security patches.
- Monitor Activity Logs: Regularly review activity logs to detect and respond to any suspicious behavior.
Common Issues and Troubleshooting
Despite careful planning, issues may arise during the setup and operation of RemoteIoT behind a firewall. Below are some common problems and solutions:
- Connection Issues: Check firewall settings and ensure that required ports are open.
- Performance Problems: Optimize server settings and reduce network congestion.
- Security Breaches: Review security protocols and update software to address vulnerabilities.
Best Practices for Maintenance
Maintaining a RemoteIoT setup behind a firewall requires regular attention and care. Below are some best practices to follow:
- Perform Regular Backups: Ensure that all critical data is backed up regularly to prevent data loss.
- Monitor System Performance: Continuously monitor system performance and address any bottlenecks.
- Train Staff: Educate your team on best practices for managing and maintaining the RemoteIoT system.
Conclusion and Next Steps
Using RemoteIoT behind a firewall with a Mac server offers a secure and efficient solution for managing IoT devices. By following the steps outlined in this article, you can successfully set up and maintain this configuration. Remember to prioritize security, regularly update your system, and adhere to best practices for optimal performance.
We encourage you to share your thoughts and experiences in the comments section below. Additionally, feel free to explore other articles on our site for more valuable insights and information. Together, let's build a safer and more connected future!
Data Source: Apple macOS Server, RemoteIoT Official Website.
![Mac Firewall Setting How To Configure It? [Stepwise Tutorial]](https://techyhost.com/wp-content/uploads/2022/12/changing-firewall-settings-mac-1.jpg)
