Are you struggling to access RemoteIoT behind a firewall using your Mac? This guide will walk you through the process step by step, ensuring seamless connectivity without compromising security. In today's interconnected world, remote IoT access has become essential for managing devices and systems from anywhere. However, firewalls can sometimes pose challenges when attempting to connect. Fortunately, with the right strategies and tools, you can overcome these obstacles.
Whether you're a network administrator, an IT professional, or someone who simply wants to manage IoT devices remotely, this article is designed to provide you with all the information you need. We'll cover everything from understanding firewalls and their impact on IoT connectivity to practical solutions that work on macOS.
By the end of this guide, you'll have the knowledge and tools necessary to securely access RemoteIoT behind a firewall using your Mac. Let's dive in and explore how you can achieve this without any hassle.
Read also:Randy Travis And Aphasia A Journey Through Challenges And Triumphs
Table of Contents
- Understanding Firewalls and Their Impact on RemoteIoT
- Why Use Mac for RemoteIoT Access?
- Preparing Your Mac for Secure IoT Access
- Using VPN Solutions to Access RemoteIoT Behind Firewall
- Configuring Port Forwarding for RemoteIoT
- SSH Tunneling for Secure IoT Connections
- Leveraging Third-Party Tools for Enhanced Connectivity
- Security Tips for RemoteIoT Access
- Common Issues and Troubleshooting
- Conclusion and Next Steps
Understanding Firewalls and Their Impact on RemoteIoT
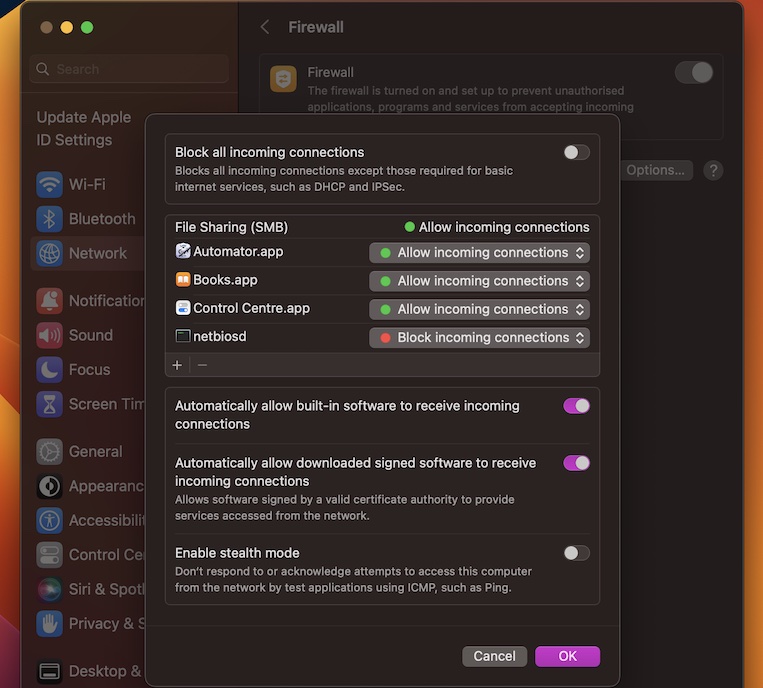
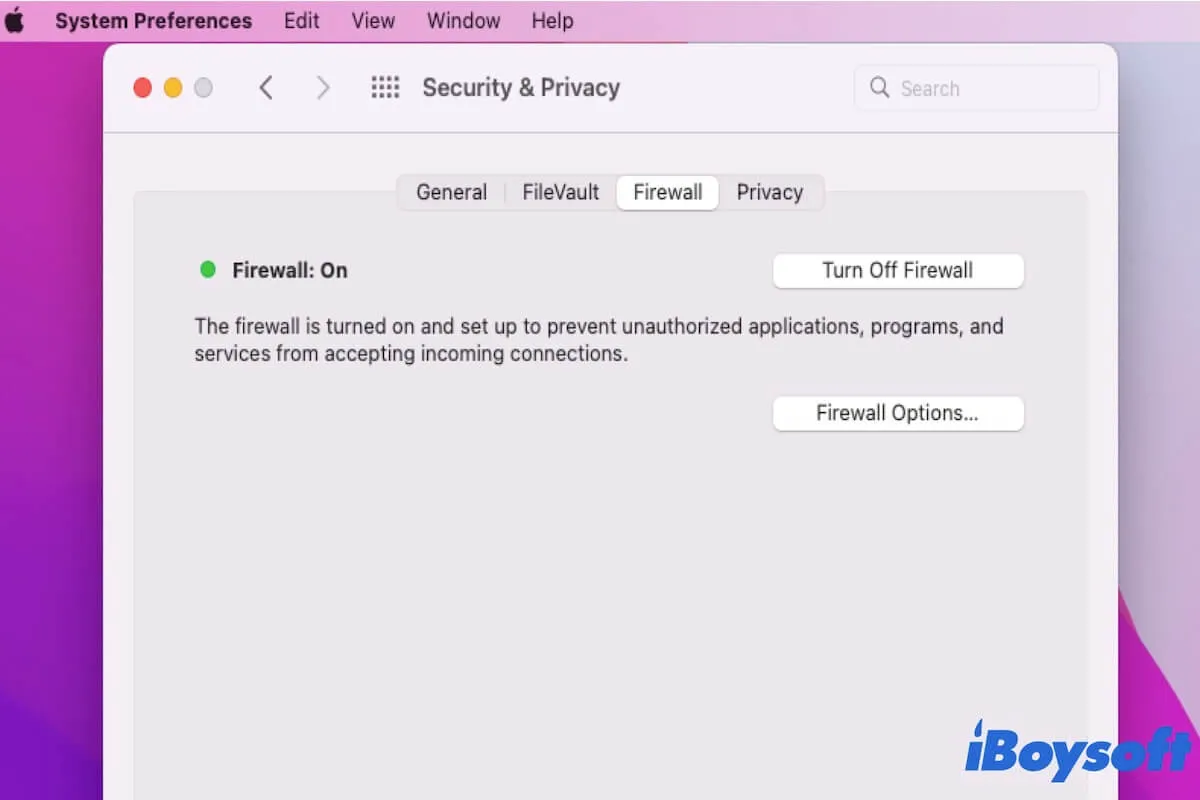
Firewalls are essential components of network security, acting as barriers between trusted internal networks and untrusted external networks like the internet. However, they can sometimes block legitimate traffic, including connections to IoT devices. When attempting to access RemoteIoT behind a firewall, you may encounter restrictions that prevent direct communication.
Key Points:
- Firewalls filter incoming and outgoing traffic based on predefined security rules.
- Some firewalls block specific ports or protocols commonly used by IoT devices.
- Understanding your firewall's configuration is crucial for troubleshooting connectivity issues.
To ensure smooth access to RemoteIoT behind a firewall, you need to identify which ports and protocols are being blocked and implement workarounds accordingly. This section will delve deeper into how firewalls impact IoT connectivity and provide practical solutions.
Types of Firewalls and Their Functions
Firewalls come in various types, each serving a specific purpose:
- Packet Filtering Firewalls: Inspect individual packets and allow or deny them based on IP addresses, ports, and protocols.
- Stateful Inspection Firewalls: Monitor active connections and ensure that only legitimate traffic passes through.
- Application-Level Gateways: Analyze application-layer traffic, such as HTTP or HTTPS, for deeper inspection.
Understanding the type of firewall you're dealing with is the first step toward resolving connectivity issues with RemoteIoT.
Why Use Mac for RemoteIoT Access?
macOS offers several advantages when it comes to accessing IoT devices behind firewalls:
Read also:William H Macy A Renowned Actor With A Legacy In Hollywood
- Native support for secure protocols like SSH and TLS.
- Integration with powerful command-line tools for advanced configurations.
- Compatibility with popular third-party applications for enhanced connectivity.
These features make macOS an ideal platform for managing RemoteIoT devices while maintaining robust security. Additionally, macOS's user-friendly interface simplifies the setup process for users of all skill levels.
Preparing Your Mac for Secure IoT Access
Before attempting to access RemoteIoT behind a firewall, ensure your Mac is properly configured:
Step 1: Update macOS and Install Necessary Software
Why it matters: Keeping your operating system and software up to date ensures compatibility with the latest security protocols and features.
- Download and install the latest macOS version from the App Store.
- Install essential tools such as Terminal, OpenSSH, and any third-party applications required for your setup.
Step 2: Configure Network Settings
Tips:
- Set up a static IP address if required by your network configuration.
- Ensure your Mac is connected to the correct network interface (Wi-Fi or Ethernet).
Using VPN Solutions to Access RemoteIoT Behind Firewall
Virtual Private Networks (VPNs) create encrypted tunnels that allow secure communication between devices, even when behind firewalls. Using a VPN is one of the most effective ways to access RemoteIoT securely.
Choosing the Right VPN Service
When selecting a VPN for RemoteIoT access, consider the following factors:
- Compatibility with macOS.
- Support for protocols such as OpenVPN or WireGuard.
- Reliable performance and minimal latency.
Setting Up a VPN on macOS
Steps:
- Download and install a reputable VPN client.
- Configure the connection settings using the provider's instructions.
- Connect to the VPN and test your RemoteIoT access.
Configuring Port Forwarding for RemoteIoT
If a firewall blocks specific ports required for RemoteIoT communication, port forwarding can help bypass these restrictions. This involves mapping external ports to internal devices on your network.
Steps to Configure Port Forwarding
- Access your router's configuration page through a web browser.
- Locate the port forwarding section and add a new rule.
- Specify the external port, internal IP address, and protocol used by RemoteIoT.
Note: Always ensure that forwarded ports are secured to prevent unauthorized access.
SSH Tunneling for Secure IoT Connections
SSH tunneling provides an encrypted connection between your Mac and RemoteIoT devices, ensuring secure communication even behind restrictive firewalls.
How SSH Tunneling Works
SSH tunnels encrypt data transmitted between devices, making it difficult for firewalls to block or intercept traffic. To set up an SSH tunnel:
- Open Terminal on your Mac.
- Use the following command:
ssh -L [local_port]:[remote_host]:[remote_port] [user]@[ssh_server]. - Replace placeholders with actual values based on your setup.
Leveraging Third-Party Tools for Enhanced Connectivity
Several third-party tools can simplify the process of accessing RemoteIoT behind firewalls:
- TunnelBear: A user-friendly VPN client for macOS.
- Ngrok: A tool for creating secure tunnels to local servers.
- TeamViewer: A remote access solution that supports IoT devices.
These tools often provide intuitive interfaces and additional features that enhance connectivity and security.
Security Tips for RemoteIoT Access
When accessing RemoteIoT behind a firewall, prioritizing security is paramount. Follow these best practices:
- Use strong, unique passwords for all devices and accounts.
- Enable two-factor authentication whenever possible.
- Regularly update firmware and software to patch vulnerabilities.
- Monitor network activity for signs of unauthorized access.
Common Issues and Troubleshooting
Despite careful planning, issues may arise when accessing RemoteIoT behind a firewall. Here are some common problems and solutions:
- Issue: Connection timeout.
Solution: Check firewall rules and ensure required ports are open. - Issue: Authentication failure.
Solution: Verify credentials and reconfigure authentication settings. - Issue: Slow performance.
Solution: Optimize network settings and consider switching to a faster VPN.
Conclusion and Next Steps
In conclusion, accessing RemoteIoT behind a firewall using your Mac is achievable with the right strategies and tools. By understanding firewalls, leveraging secure protocols, and implementing best practices, you can ensure seamless connectivity while maintaining robust security.
We encourage you to share your experiences and ask questions in the comments section below. Additionally, explore other articles on our site for more tips and insights into IoT and network management. Together, let's build a safer, more connected digital world!
![Mac Firewall Setting How To Configure It? [Stepwise Tutorial]](https://techyhost.com/wp-content/uploads/2022/12/changing-firewall-settings-mac-1.jpg)