Using RemoteIoT behind a firewall on Mac can seem challenging, but with the right steps, it becomes a straightforward process. Whether you're managing IoT devices remotely or ensuring secure connections, understanding how to navigate firewalls is essential. This article will guide you through every aspect, ensuring your setup remains efficient and secure.
As more businesses and individuals rely on IoT devices for daily operations, managing them remotely becomes crucial. However, firewalls often pose obstacles, especially when working on a Mac. This guide aims to simplify the process, offering step-by-step instructions to help you configure your system effectively.
Throughout this article, we'll explore the technical aspects of configuring RemoteIoT, troubleshooting common issues, and ensuring data security. By the end, you'll have a thorough understanding of how to use RemoteIoT behind a firewall on your Mac, empowering you to manage your IoT devices with confidence.
Read also:Julia Rose Shag Mag The Ultimate Guide To Her Life Career And Influence
Table of Contents
- Introduction to RemoteIoT and Firewalls
- Understanding Firewalls on Mac
- Overview of RemoteIoT
- Setting Up RemoteIoT Behind Firewall
- Enhancing Security Measures
- Troubleshooting Common Issues
- Optimizing Performance
- Advanced Configuration Tips
- Best Practices for RemoteIoT Management
- Conclusion and Call to Action
Introduction to RemoteIoT and Firewalls
RemoteIoT is a powerful tool that allows users to manage IoT devices from a distance, providing flexibility and convenience. However, firewalls can restrict access, making it essential to understand how to configure them properly. For Mac users, this process involves several key steps to ensure seamless operation.
Firewalls are designed to protect networks by filtering incoming and outgoing traffic based on predetermined security rules. While they enhance security, they can sometimes block legitimate connections. Learning how to configure your firewall for RemoteIoT ensures that your IoT devices remain accessible without compromising security.
Understanding Firewalls on Mac
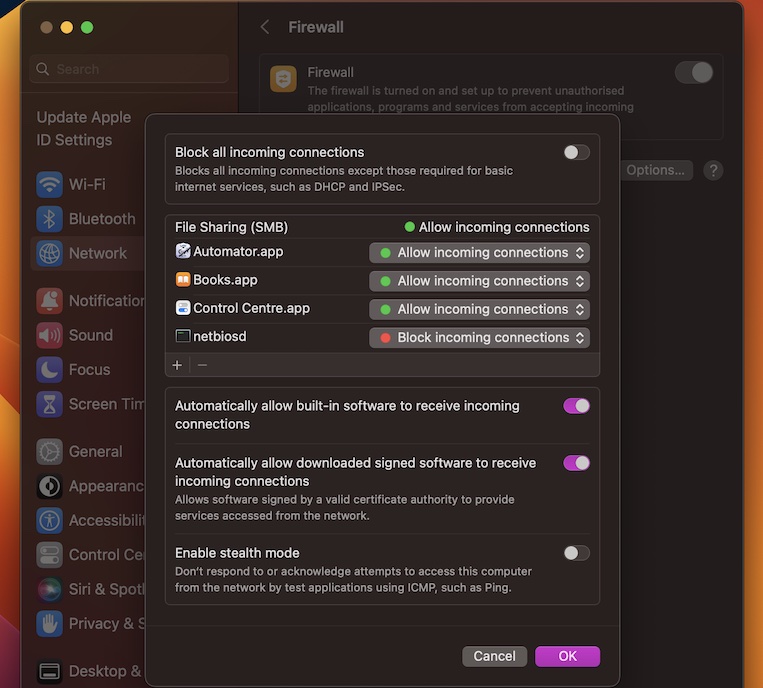
MacOS comes equipped with a built-in firewall that offers robust protection. To use RemoteIoT behind a firewall, you need to understand its features and settings. Here's a brief overview:
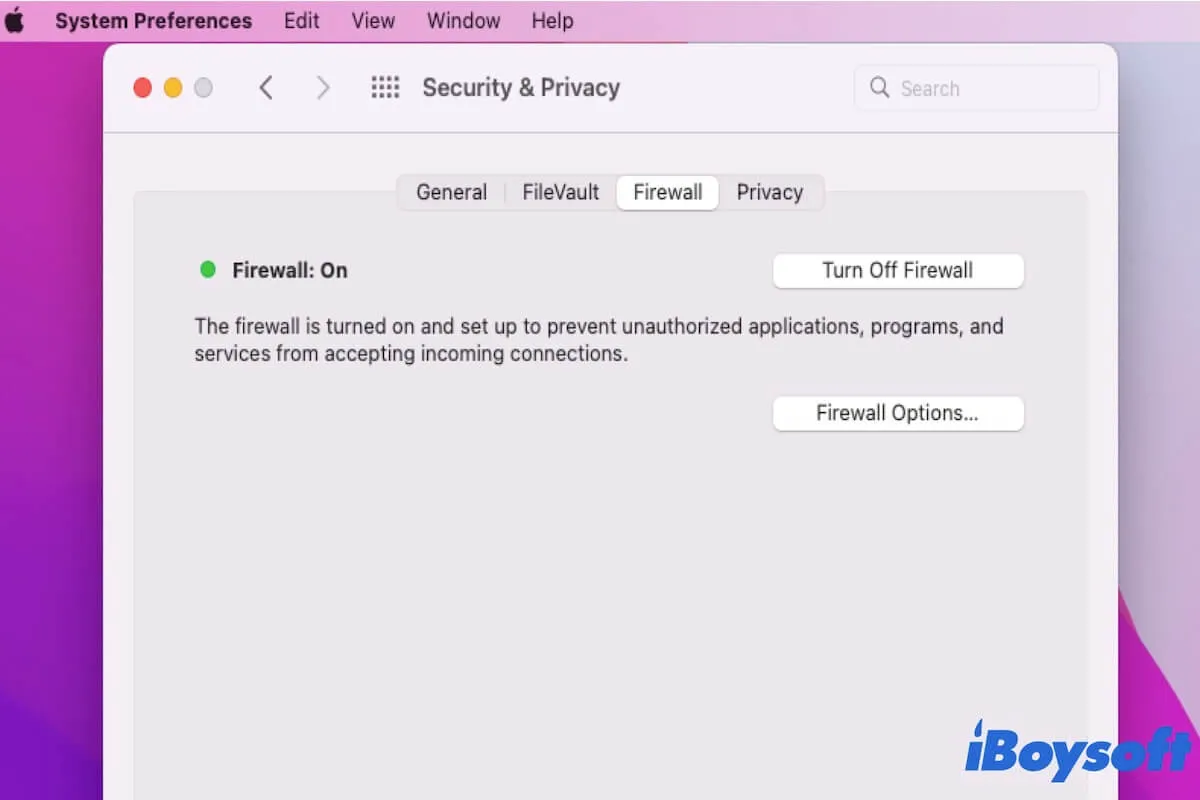
- Firewall Settings: Located in System Preferences > Security & Privacy > Firewall.
- Block All Incoming Connections: This option enhances security but may block necessary connections.
- Allow Specific Applications: Configure the firewall to allow RemoteIoT and related applications.
By fine-tuning these settings, you can create a balance between security and functionality, ensuring RemoteIoT operates smoothly.
Overview of RemoteIoT
RemoteIoT is a versatile platform designed to manage IoT devices remotely. It supports a wide range of devices and protocols, making it suitable for various applications. Key features include:
- Real-time data monitoring.
- Secure device management.
- Customizable dashboards for better visualization.
Understanding these features helps you leverage RemoteIoT's full potential, even when operating behind a firewall.
Read also:Gail Ogrady A Comprehensive Guide To Her Career Achievements And Legacy
Setting Up RemoteIoT Behind Firewall
Step 1: Configuring Network Settings
Before configuring the firewall, ensure your network settings are optimized for RemoteIoT. Follow these steps:
- Check IP Configuration: Ensure your Mac has a static IP address to maintain consistent connectivity.
- Set Up Port Forwarding: Configure your router to forward necessary ports to your Mac.
- Test Network Connectivity: Use tools like ping or traceroute to verify network stability.
These steps lay the foundation for a stable connection, preparing your system for firewall configuration.
Step 2: Adjusting Firewall Rules
Adjusting firewall rules is crucial for allowing RemoteIoT to function correctly. Here's how:
- Open Firewall Settings: Navigate to System Preferences > Security & Privacy > Firewall.
- Add RemoteIoT to Allowed Applications: Click "Firewall Options" and add the RemoteIoT application.
- Create Custom Rules: Define specific rules to allow traffic on required ports.
By carefully configuring these rules, you ensure that RemoteIoT can communicate with IoT devices without being blocked by the firewall.
Enhancing Security Measures
Security is paramount when using RemoteIoT behind a firewall. Here are some tips to enhance protection:
- Use Strong Passwords: Implement complex passwords for all accounts and devices.
- Enable Two-Factor Authentication: Add an extra layer of security to your RemoteIoT account.
- Regularly Update Software: Keep both RemoteIoT and MacOS updated to patch vulnerabilities.
Implementing these measures ensures your system remains secure while maintaining functionality.
Troubleshooting Common Issues
Despite careful configuration, issues may arise. Here's how to address common problems:
- Connection Errors: Verify port forwarding and firewall settings.
- Slow Performance: Optimize network settings and reduce unnecessary traffic.
- Security Alerts: Review firewall logs to identify and resolve potential threats.
By addressing these issues promptly, you maintain a smooth and secure RemoteIoT setup.
Optimizing Performance
To ensure optimal performance, consider the following tips:
- Monitor Network Traffic: Use tools like Wireshark to analyze and optimize data flow.
- Limit Background Applications: Close unnecessary programs to free up system resources.
- Regular Maintenance: Perform routine checks and updates to maintain system health.
These practices help you achieve the best possible performance from your RemoteIoT setup.
Advanced Configuration Tips
For advanced users, here are some additional configuration tips:
- Set Up a Virtual Private Network (VPN): Enhance security and bypass firewall restrictions.
- Implement Quality of Service (QoS): Prioritize RemoteIoT traffic for better performance.
- Use SSH Tunnels: Create secure tunnels for encrypted communication.
These advanced techniques provide greater control and security for your RemoteIoT setup.
Best Practices for RemoteIoT Management
Adopting best practices ensures long-term success with RemoteIoT. Consider the following:
- Document Configuration Settings: Keep detailed records for easy reference.
- Regularly Review Security Policies: Stay updated on the latest threats and countermeasures.
- Engage in Continuous Learning: Stay informed about advancements in IoT and cybersecurity.
By following these practices, you maintain a robust and secure RemoteIoT environment.
Conclusion and Call to Action
In conclusion, using RemoteIoT behind a firewall on Mac requires careful configuration and attention to security. By following the steps outlined in this guide, you can achieve a seamless and secure setup. Remember to regularly review and update your configuration to adapt to changing requirements.
We encourage you to share your experiences and insights in the comments below. Your feedback helps us improve and provides valuable information to other users. Additionally, explore our other articles for more tips and guides on managing IoT devices effectively.
Stay connected and keep innovating!
![Mac Firewall Setting How To Configure It? [Stepwise Tutorial]](https://techyhost.com/wp-content/uploads/2022/12/changing-firewall-settings-mac-1.jpg)